filmov
tv
WebKit RegExp Exploit addrof() walk-through
Показать описание
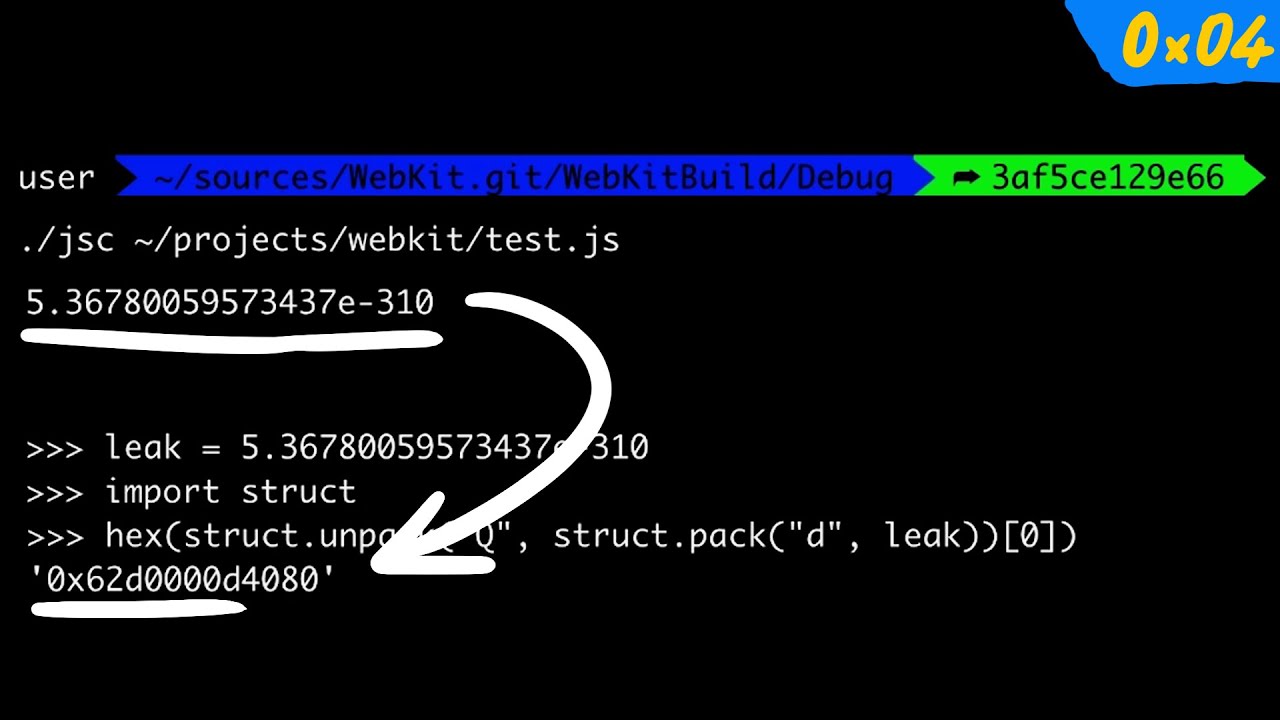
Part 4: We finally look at the actual exploit code. We start by understanding the addrof() primitive used to leak the address of a JavaScript object in memory.
-=[ 🕴️Advertisement ]=-
-=[ ❤️ Support ]=-
-=[ 🔴 Stuff I use ]=-
-=[ 🐕 Social ]=-
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#browserexploitation
-=[ 🕴️Advertisement ]=-
-=[ ❤️ Support ]=-
-=[ 🔴 Stuff I use ]=-
-=[ 🐕 Social ]=-
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#browserexploitation
WebKit RegExp Exploit addrof() walk-through
Arbitrary Read and Write in WebKit Exploit
Burp + regex = vuln||error
Preparing for Stage 2 of a WebKit exploit
Hacking Browsers - Setup and Debug JavaScriptCore / WebKit
Safari (java script core) javascript engine exploit poc
The fakeobj() Primitive: Turning an Address Leak into a Memory Corruption
Unauth'd RCE, 'Regexploits', Post-Spectre Web, & SigStore Signing - ASW #143
101 - Big Bounties by Exploiting WebKit's CSP & Concrete CMS Bugs [Bounty Hunting Podcast]
Recent Tor 6.06 Browser Exploit vs EMET, then with an IAT Parsing Payload
Just-in-time Compiler in JavaScriptCore (WebKit)
New Series: Getting Into Browser Exploitation - browser 0x00
CSS Webkit//Webkit Text Css. #html #htmlcss #css #short #shortvideo #shorts #programming #coding
Browser update Exploit
Revisiting JavaScriptCore Internals: boxed vs. unboxed
Exploit Fails? Debug Your Shellcode - bin 0x2B
Simple Use After Free Exploitation [Hackvent 2022 - Day 21]
What do Nintendo Switch and iOS 9.3 have in common? CVE-2016-4657 walk-through
I made every video I ever wanted to make
New Hackbar modified by Ph.Hitachi + LiveHTTPHeader & TamperData
Browser hacking: Fixing error propagation in LibWeb
Live Hacking - Internetwache CTF 2016 - exp50, exp70, exp80
Attacking Client-Side JIT Compilers
The Butterfly of JSObject
Комментарии
 0:13:31
0:13:31
 0:09:40
0:09:40
 0:06:17
0:06:17
 0:14:33
0:14:33
 0:11:36
0:11:36
 0:00:22
0:00:22
 0:15:59
0:15:59
 0:28:43
0:28:43
 0:38:11
0:38:11
 0:01:23
0:01:23
 0:09:50
0:09:50
 0:09:46
0:09:46
 0:00:57
0:00:57
 0:09:29
0:09:29
 0:08:59
0:08:59
 0:10:01
0:10:01
 0:28:51
0:28:51
 0:18:44
0:18:44
 0:14:29
0:14:29
 0:02:52
0:02:52
 0:34:22
0:34:22
 0:16:56
0:16:56
 0:42:34
0:42:34
 0:10:56
0:10:56