filmov
tv
Oracle Database Exploitation with Metasploit | CTF Walkthrough

Показать описание
In this video walk-through, we covered Oracle Database Exploitation with Metasploit framework and oracle database attacking tool as part of Pwn with Metasploit from Hackthebox. Silo machine from hackthebox platform focuses mainly on leveraging Oracle to obtain a shell and escalate privileges. It was intended to be completed manually using various tools, however Oracle Database Attack Tool greatly simplifies the process, reducing the difficulty of the machine substantially.
**********
Receive Cyber Security Field Notes, Certification Notes and Special Training Videos
*******
Writeup
******
Instagram
Twitter
Facebook
LinkedIn
Website
Patreon
Backup channel
My Movie channel:
******
**********
Receive Cyber Security Field Notes, Certification Notes and Special Training Videos
*******
Writeup
******
Website
Patreon
Backup channel
My Movie channel:
******
Oracle Database Exploitation with Metasploit | CTF Walkthrough
Hacking an Oracle Database and How to Prevent It
Metasploit-Using the database to store and analyze pentesting result
Hacking with metasploit #commands #kali
Oracle MySQL UDF for Microsoft Windows Metasploit Payload Execution
Oracle Database TNS Poisoning Attacks CVE-2012-1675
Un-Hacking The Oracle Database
Metasploit Hacking Demo (includes password cracking)
Printer Driver Exploitation with Metasploit | CTF Walkthrough
Adding New Latest Exploits from exploit-db.com to Metasploit
The Tools Hackers Are Using Against Your Oracle Database
Tips on Protection from Oracle TNS Poisoning Zero Day Vulnerability
Metasploit Database Command
Basic Exploitation with Metasploit: Windows: HTTP File Server
Oracle Reports 11g Remote Shell - CVE-2012-3152
CVE-2012-1675 Oracle Database TNS Poison 0Day Demonstration
Metasploit Post Exploitation With DbVisualizer Modules
CVE-2013-1488 Oracle Java Applet Driver Manager Vulnerability Metasploit Demo
Master in Hacking with Metasploit #33 scanner auxiliary modules Mysql Brute force Attack
SQL Injections are scary!! (hacking tutorial for beginners)
Nostromo Web Server Exploit | CTF Walkthrough | Pwn With Metasploit | Ethical Hacking
Nmap Tutorial to find Network Vulnerabilities
Metasploit: WebApp Exploits Vulnerable: Webapp XI
Oracle Attack
Комментарии
 0:17:31
0:17:31
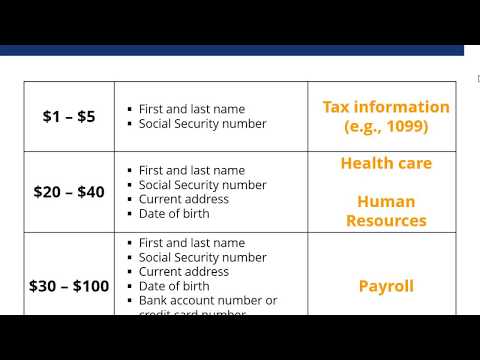 1:07:34
1:07:34
 0:03:08
0:03:08
 0:00:16
0:00:16
 0:03:26
0:03:26
 0:50:03
0:50:03
 0:26:55
0:26:55
 0:17:50
0:17:50
 0:23:42
0:23:42
 0:03:39
0:03:39
 1:03:23
1:03:23
 0:36:57
0:36:57
 0:04:24
0:04:24
 0:03:17
0:03:17
 0:03:17
0:03:17
 0:04:39
0:04:39
 0:01:55
0:01:55
 0:02:11
0:02:11
 0:01:51
0:01:51
 0:10:14
0:10:14
 0:30:21
0:30:21
 0:17:09
0:17:09
 0:02:14
0:02:14
 0:03:24
0:03:24