filmov
tv
How to Execute a Complex MySQL Query in Rails Using ActiveRecord

Показать описание
Learn how to run complex MySQL queries in a Ruby on Rails application utilizing the capabilities of ActiveRecord. This guide covers essentials for executing raw SQL and integrating it seamlessly within Rails.
---
Disclaimer/Disclosure: Some of the content was synthetically produced using various Generative AI (artificial intelligence) tools; so, there may be inaccuracies or misleading information present in the video. Please consider this before relying on the content to make any decisions or take any actions etc. If you still have any concerns, please feel free to write them in a comment. Thank you.
---
How to Execute a Complex MySQL Query in Rails Using ActiveRecord
Using complex MySQL queries within a Ruby on Rails application can sometimes seem daunting, especially when you're leveraging ActiveRecord. However, Rails provides robust mechanisms to execute raw SQL queries, making it straightforward and efficient.
Why Use Raw SQL in Rails?
ActiveRecord, the default ORM for Rails, simplifies interactions with the database using a high-level API. However, scenarios may arise where:
Performance optimization: Certain operations are more efficiently executed as raw SQL.
Complex queries: Some intricate queries are easier to write in SQL directly.
Using database-specific features: Need to leverage database-specific optimizations or features not supported natively by ActiveRecord.
Executing Raw SQL with ActiveRecord
ActiveRecord makes it convenient to execute raw SQL queries. Here are a few methods to do so:
Using find_by_sql
The find_by_sql method allows execution of a SQL statement and returns an array of model instances.
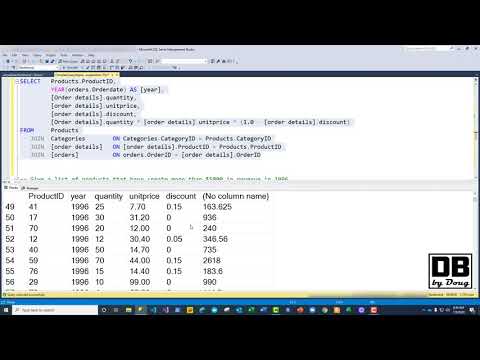
[[See Video to Reveal this Text or Code Snippet]]
[[See Video to Reveal this Text or Code Snippet]]
Using pluck and select
When you need specific columns or values, pluck and select methods can simplify the job.
[[See Video to Reveal this Text or Code Snippet]]
Handling SQL Injection
When executing raw SQL queries, it's critical to be aware of SQL injection vulnerabilities. Always sanitize inputs:
Use placeholders and bindings: ["SELECT * FROM users WHERE name = ?", name]
Utilize ActiveRecord’s methods wherever possible.
Conclusion
---
Disclaimer/Disclosure: Some of the content was synthetically produced using various Generative AI (artificial intelligence) tools; so, there may be inaccuracies or misleading information present in the video. Please consider this before relying on the content to make any decisions or take any actions etc. If you still have any concerns, please feel free to write them in a comment. Thank you.
---
How to Execute a Complex MySQL Query in Rails Using ActiveRecord
Using complex MySQL queries within a Ruby on Rails application can sometimes seem daunting, especially when you're leveraging ActiveRecord. However, Rails provides robust mechanisms to execute raw SQL queries, making it straightforward and efficient.
Why Use Raw SQL in Rails?
ActiveRecord, the default ORM for Rails, simplifies interactions with the database using a high-level API. However, scenarios may arise where:
Performance optimization: Certain operations are more efficiently executed as raw SQL.
Complex queries: Some intricate queries are easier to write in SQL directly.
Using database-specific features: Need to leverage database-specific optimizations or features not supported natively by ActiveRecord.
Executing Raw SQL with ActiveRecord
ActiveRecord makes it convenient to execute raw SQL queries. Here are a few methods to do so:
Using find_by_sql
The find_by_sql method allows execution of a SQL statement and returns an array of model instances.
[[See Video to Reveal this Text or Code Snippet]]
[[See Video to Reveal this Text or Code Snippet]]
Using pluck and select
When you need specific columns or values, pluck and select methods can simplify the job.
[[See Video to Reveal this Text or Code Snippet]]
Handling SQL Injection
When executing raw SQL queries, it's critical to be aware of SQL injection vulnerabilities. Always sanitize inputs:
Use placeholders and bindings: ["SELECT * FROM users WHERE name = ?", name]
Utilize ActiveRecord’s methods wherever possible.
Conclusion
 0:08:33
0:08:33
 0:49:56
0:49:56
 0:00:16
0:00:16
 0:01:26
0:01:26
 0:25:16
0:25:16
 0:04:33
0:04:33
 0:08:35
0:08:35
 0:00:10
0:00:10
 0:04:58
0:04:58
 0:54:41
0:54:41
 0:01:38
0:01:38
 0:32:09
0:32:09
 0:00:13
0:00:13
 0:16:38
0:16:38
 0:18:40
0:18:40
 0:00:31
0:00:31
 0:00:23
0:00:23
 0:02:05
0:02:05
 0:00:12
0:00:12
 0:08:08
0:08:08
 0:00:39
0:00:39
 0:44:44
0:44:44
 0:00:11
0:00:11
 0:00:13
0:00:13