filmov
tv
Detecting & Responding to Pandas and Bears:

Показать описание
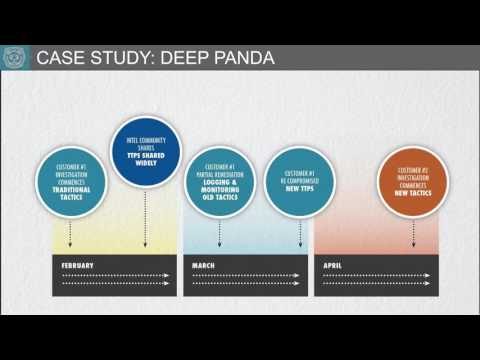
30% of incident response investigations conducted by our team over the past two years have had multiple attack groups operating at the same time within the same organization, and this number is likely to increase in the future. Do you know how to identify and remove multiple attackers within your environment?
This presentation focuses on a recent investigation where the victim was simultaneously under attack by two separate attack groups, each with varying goals and TTPs. We’ll demonstrate the critical role played by threat intelligence in identifying the attackers and how using this information allows responders and security teams to tailor their remediation tactics and implementation for success. We’ll share approaches you can use and when to apply them.
Attendees will also learn how to conduct adversary-based hunting operations using existing technology within your organization; improve authentication credential protection during live IR, and prepare for detection of future attacks.
Christopher Scott, Director, CrowdStrike Services
Wendi Whitmore, VP IBM
Christopher Scott has 18 years of Fortune 500/DoD/DIB
business proficiency, including more than eight years of targeted threat detection and prevention expertise. Christopher supports a variety of engagements at CrowdStrike that include: proactive and reactive security services, incident response, data loss prevention, business continuity and disaster recovery processes.
Wendi Whitmore has over 15 years of experience in
the computer security industry responding to critical
security breaches and providing customers with solutions
to complex adversary problems.
SANS THREAT HUNTING AND INCIDENT RESPONSE COURSES
This presentation focuses on a recent investigation where the victim was simultaneously under attack by two separate attack groups, each with varying goals and TTPs. We’ll demonstrate the critical role played by threat intelligence in identifying the attackers and how using this information allows responders and security teams to tailor their remediation tactics and implementation for success. We’ll share approaches you can use and when to apply them.
Attendees will also learn how to conduct adversary-based hunting operations using existing technology within your organization; improve authentication credential protection during live IR, and prepare for detection of future attacks.
Christopher Scott, Director, CrowdStrike Services
Wendi Whitmore, VP IBM
Christopher Scott has 18 years of Fortune 500/DoD/DIB
business proficiency, including more than eight years of targeted threat detection and prevention expertise. Christopher supports a variety of engagements at CrowdStrike that include: proactive and reactive security services, incident response, data loss prevention, business continuity and disaster recovery processes.
Wendi Whitmore has over 15 years of experience in
the computer security industry responding to critical
security breaches and providing customers with solutions
to complex adversary problems.
SANS THREAT HUNTING AND INCIDENT RESPONSE COURSES
 0:37:14
0:37:14
 0:16:09
0:16:09
 0:03:41
0:03:41
 0:06:29
0:06:29
 0:00:55
0:00:55
 0:01:16
0:01:16
 0:00:59
0:00:59
 0:01:00
0:01:00
 11:54:56
11:54:56
 0:24:56
0:24:56
 0:00:41
0:00:41
 0:00:50
0:00:50
 0:47:30
0:47:30
 0:03:22
0:03:22
 0:04:57
0:04:57
 0:12:13
0:12:13
 0:09:21
0:09:21
 0:36:49
0:36:49
 0:02:35
0:02:35
 0:00:56
0:00:56
 0:06:29
0:06:29
 0:05:24
0:05:24
 0:01:31
0:01:31
 0:06:29
0:06:29