filmov
tv
How to create an Application Whitelist Policy in Windows
Показать описание
Text Source
#POLICY #WINDOWS #WHITELIST #APPLICATION #CREATE #HOW
How to create an Application Whitelist Policy in Windows
In Windows it is possible to configure two different methods that determine whether an application should be allowed to run. The first method, known as blacklisting, is when you allow all applications to run by default except for those you specifically do not allow. The other, and more secure, method is called whitelisting, which blocks every application from running by default, except for those you explicitly allow.
With the wide distribution of computer ransomware and other malware infections and the high costs of recovering from them, a very strong computer protection method is whitelisting. This allows you to block all programs by default and then setup rules that specifically allow only certain programs to run.
Though easy to setup initially, whitelisting can be burdensome as you will need to add new rules every time you install a new program or want to allow a program to run. Personally, I feel if you are willing to put the time and effort into using whitelisting, the chances of a computer infection damaging your computer becomes minimal.
This tutorial will walk you through setting up whitelisting using Software Restriction Policies so that only specified applications are able to run on your computer. Though this guide will be geared towards individual users, this same approach can be used in the enterprise by pushing these policies to a Windows domain.
The method we use to create the application whitelist policy is through the Security Policy Editor. Unfortunately, this tool is not available in Home versions of Windows. Therefore, you may want to instead use a program like CryptoPrevent to configure a blacklisting policy for you.
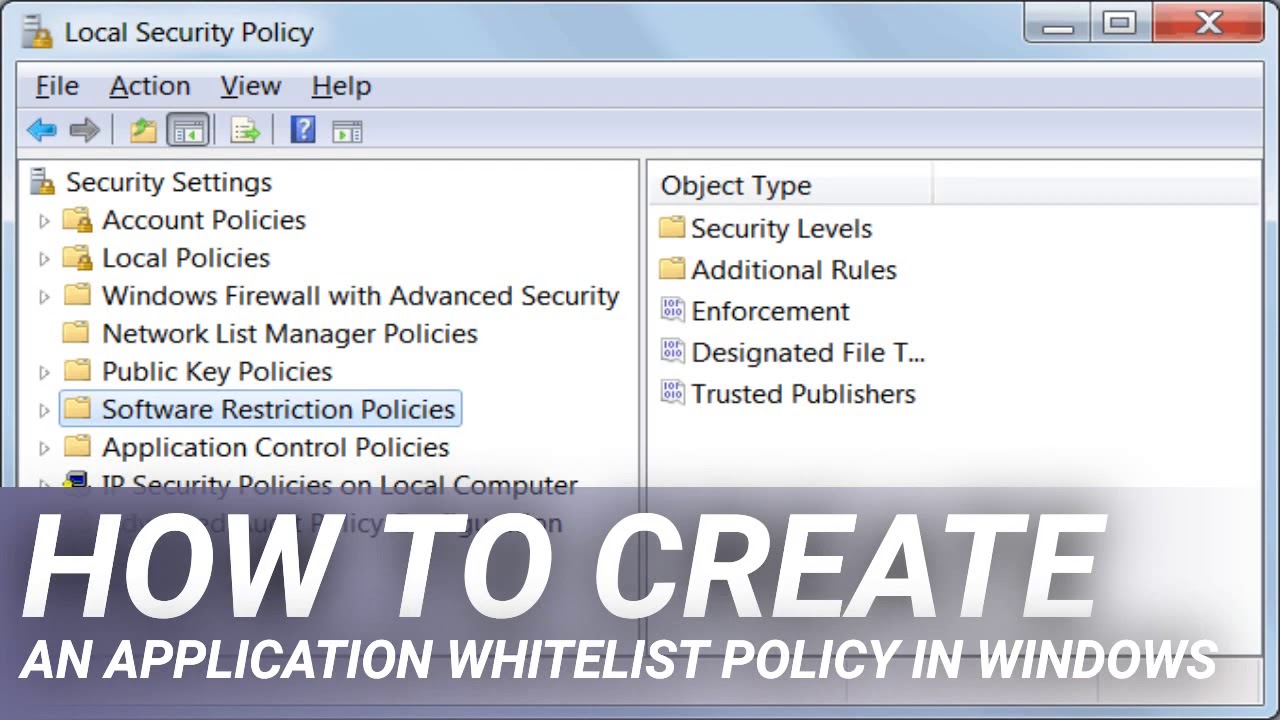
To begin creating our application whitelist, click on the Software Restriction Policies category. If you have never created a software restriction policy in the past, you will see a screen similar to the one below.
To create the new policy, right click on the Software Restriction Policies category and select the New Software Restriction Policies option as shown below.
The first thing you need to do is configure the Enforcement section. This section allows us to specify general settings on how these restriction policies will be configured. To get started, click on the Enforcement object type as indicated by the blue arrow above.
I suggest that you leave the settings like they are for now. This allows you to create a strong policy, without the issues the may be caused by blocking DLLs. When you are done configuring these settings, click on the OK button.
You will now be back at the main Software Restriction Policies window as shown in Figure 5. We now want to configure what file types will be considered an executable and thus blocked. To do this click on the Designated File Types object.
This will open the properties window for the designated file types that will be considered as an executable and therefore blocked by the software restriction policy that you are creating.
Unfortunately, the above the list is not as exhaustive as you would like and includes an extension that should be removed. First, scroll through the above list of file extensions and remove the LNK extension from the list. To remove the extension, left-click on it once and then click on the Remove button. If you do not remove this extension, then all shortcuts will fail to work after you create our whitelist.
Now you want to add some extra extensions that are known to be used to install malware and ransomware. To add an extension, simply add it to the File Extension field and click on the Add button. When adding an extension, do not include the period. For example, to exclude powershell scripts, you would enter PS1 into the field and click on the Add button.
We will now be back at the main Software Restrictions Policy section as shown in Figure 8 below. At this point, you need to configure the default policy that decides whether the file types configured in figure 7 will be automatically blocked or allowed to run. To do this, click on the Security Levels option as indicated by the blue arrow below.
When you double-click on the Security Levels category, you will be brought to the screen below that has three security levels you can apply to your software restriction policies.
In order to select which level should be used…
#POLICY #WINDOWS #WHITELIST #APPLICATION #CREATE #HOW
How to create an Application Whitelist Policy in Windows
In Windows it is possible to configure two different methods that determine whether an application should be allowed to run. The first method, known as blacklisting, is when you allow all applications to run by default except for those you specifically do not allow. The other, and more secure, method is called whitelisting, which blocks every application from running by default, except for those you explicitly allow.
With the wide distribution of computer ransomware and other malware infections and the high costs of recovering from them, a very strong computer protection method is whitelisting. This allows you to block all programs by default and then setup rules that specifically allow only certain programs to run.
Though easy to setup initially, whitelisting can be burdensome as you will need to add new rules every time you install a new program or want to allow a program to run. Personally, I feel if you are willing to put the time and effort into using whitelisting, the chances of a computer infection damaging your computer becomes minimal.
This tutorial will walk you through setting up whitelisting using Software Restriction Policies so that only specified applications are able to run on your computer. Though this guide will be geared towards individual users, this same approach can be used in the enterprise by pushing these policies to a Windows domain.
The method we use to create the application whitelist policy is through the Security Policy Editor. Unfortunately, this tool is not available in Home versions of Windows. Therefore, you may want to instead use a program like CryptoPrevent to configure a blacklisting policy for you.
To begin creating our application whitelist, click on the Software Restriction Policies category. If you have never created a software restriction policy in the past, you will see a screen similar to the one below.
To create the new policy, right click on the Software Restriction Policies category and select the New Software Restriction Policies option as shown below.
The first thing you need to do is configure the Enforcement section. This section allows us to specify general settings on how these restriction policies will be configured. To get started, click on the Enforcement object type as indicated by the blue arrow above.
I suggest that you leave the settings like they are for now. This allows you to create a strong policy, without the issues the may be caused by blocking DLLs. When you are done configuring these settings, click on the OK button.
You will now be back at the main Software Restriction Policies window as shown in Figure 5. We now want to configure what file types will be considered an executable and thus blocked. To do this click on the Designated File Types object.
This will open the properties window for the designated file types that will be considered as an executable and therefore blocked by the software restriction policy that you are creating.
Unfortunately, the above the list is not as exhaustive as you would like and includes an extension that should be removed. First, scroll through the above list of file extensions and remove the LNK extension from the list. To remove the extension, left-click on it once and then click on the Remove button. If you do not remove this extension, then all shortcuts will fail to work after you create our whitelist.
Now you want to add some extra extensions that are known to be used to install malware and ransomware. To add an extension, simply add it to the File Extension field and click on the Add button. When adding an extension, do not include the period. For example, to exclude powershell scripts, you would enter PS1 into the field and click on the Add button.
We will now be back at the main Software Restrictions Policy section as shown in Figure 8 below. At this point, you need to configure the default policy that decides whether the file types configured in figure 7 will be automatically blocked or allowed to run. To do this, click on the Security Levels option as indicated by the blue arrow below.
When you double-click on the Security Levels category, you will be brought to the screen below that has three security levels you can apply to your software restriction policies.
In order to select which level should be used…
 0:10:04
0:10:04
 0:16:11
0:16:11
 0:06:01
0:06:01
 0:08:28
0:08:28
 0:00:52
0:00:52
 0:07:52
0:07:52
 0:17:50
0:17:50
 0:08:16
0:08:16
 2:10:54
2:10:54
 3:00:49
3:00:49
 0:00:47
0:00:47
 0:09:56
0:09:56
 0:08:03
0:08:03
 0:00:38
0:00:38
 0:00:59
0:00:59
 0:00:16
0:00:16
 0:19:18
0:19:18
 0:08:31
0:08:31
 0:09:34
0:09:34
 0:14:47
0:14:47
 0:00:14
0:00:14
 0:04:19
0:04:19
 0:06:10
0:06:10
 0:00:14
0:00:14