filmov
tv
[BSL2022] Perfect data exfiltration techniques - Éric Filiol
Показать описание
The recent evolution of malware attack includes more and more data exfiltration. While the market of DLP (Data Prevention) is developing, most of the techniques are still in their infancy and thus are easy to bypass.
Then the attacker has to face several critical issues than can trigger alert and block the exfiltration :
1. Data may be analyzed so semantic detection (keyword) can be enforced
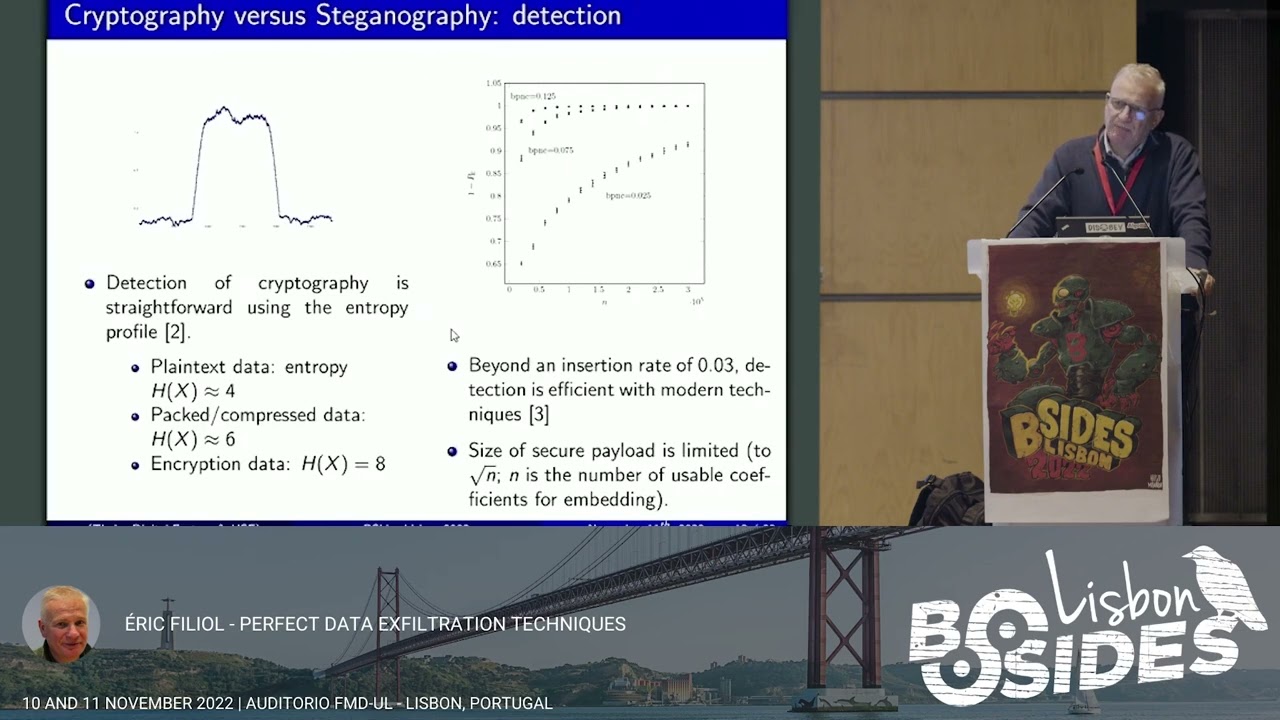
2. Encrypting data before exfiltration is likely to be detected by a simple entropy profile test (however it is rarely in place)
3. Encryption means a secret key that can be recovered during static or dynamic analysis
4. All outbound traffic may encrypted automatically and this encryption it out-of-control for this attacker
5. Known exfiltration techniques (steganography, covert channels) drastically limit the amount of data to exfiltrate without detection (up to a few kilobytes)
6. Users’ behaviors may be analyzed to detect suspect actions betraying data exfiltration
This talk intends to show how an attacker could exfiltrate sensitive data while bypassing all these issues by using different innovative malicious cryptography techniques. These techniques may also be considered by malware designers to make ransomware techniques evolve in a more critical way.
Then the attacker has to face several critical issues than can trigger alert and block the exfiltration :
1. Data may be analyzed so semantic detection (keyword) can be enforced
2. Encrypting data before exfiltration is likely to be detected by a simple entropy profile test (however it is rarely in place)
3. Encryption means a secret key that can be recovered during static or dynamic analysis
4. All outbound traffic may encrypted automatically and this encryption it out-of-control for this attacker
5. Known exfiltration techniques (steganography, covert channels) drastically limit the amount of data to exfiltrate without detection (up to a few kilobytes)
6. Users’ behaviors may be analyzed to detect suspect actions betraying data exfiltration
This talk intends to show how an attacker could exfiltrate sensitive data while bypassing all these issues by using different innovative malicious cryptography techniques. These techniques may also be considered by malware designers to make ransomware techniques evolve in a more critical way.
![[BSL2022] Perfect data](https://i.ytimg.com/vi/HF1Cjt1RPV4/hqdefault.jpg) 0:42:54
0:42:54
 0:37:44
0:37:44
 0:10:24
0:10:24
 0:45:09
0:45:09
 0:32:36
0:32:36
 0:55:18
0:55:18
 1:01:31
1:01:31
 1:17:17
1:17:17