filmov
tv
What are Digital Signatures and How Do They Work?

Показать описание
What is a Digital Signature? In this animation, we will explain how digital signatures work using cryptography.
In some ways, digital signatures do what their names suggest: they provide validation in the same way signatures do, in digital form.
Thanks for watching!
Lisk makes it easy for developers to build and deploy blockchain applications in JavaScript.
👨💻👩💻 For developers:
👫Join our community channels:
In some ways, digital signatures do what their names suggest: they provide validation in the same way signatures do, in digital form.
Thanks for watching!
Lisk makes it easy for developers to build and deploy blockchain applications in JavaScript.
👨💻👩💻 For developers:
👫Join our community channels:
What are Digital Signatures and How Do They Work?
What are Digital Signatures? - Computerphile
2 - Cryptography Basics - Digital Signature
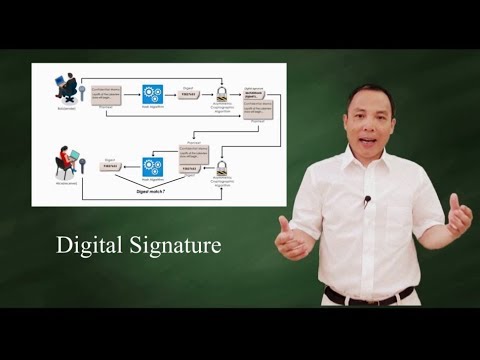
Digital Signatures
Digital Signatures and Digital Certificates
E-Signatures vs. Digital Signatures (In About A Minute)
What is digital signature?
What are Digital Signatures and How Do They Work?
Hashing and Digital Signatures - CompTIA Security+ SY0-701 - 1.4
What are Digital Signatures and why are they so important?
Digital Signatures - Data authenticity and integrity protection
CertMike Explains Digital Signatures
What are Bitcoin Digital Signatures
How to make Electronic Signature
Digital Signature | Blockchain
Why digital certificate?
Digital Signature Algorithm (DSA) - Cryptography - Practical TLS
How to Create Digital Signatures in Word – Quick and Easy Tutorial – Transparent Background
Electronic Signature vs Digital Signature? | Adobe Acrobat
Bitcoin - Digital Signatures
Lecture 18: Digital Signatures and Security Services by Christof Paar
What are Digital Signatures ? - Cryptography - Cyber Security - CSE4003
What is digital Signature and how it works | Properties of digital signature
DSA Algorithm | DSA Algorithm Explained | Digital Signature Algorithm | Simplilearn
Комментарии
 0:02:52
0:02:52
 0:10:17
0:10:17
 0:05:17
0:05:17
 0:03:36
0:03:36
 0:11:22
0:11:22
 0:01:26
0:01:26
 0:05:03
0:05:03
 0:02:11
0:02:11
 0:10:24
0:10:24
 0:01:23
0:01:23
 0:09:27
0:09:27
 0:11:11
0:11:11
 0:01:12
0:01:12
 0:16:10
0:16:10
 0:03:37
0:03:37
 0:07:33
0:07:33
 0:05:47
0:05:47
 0:04:29
0:04:29
 0:01:22
0:01:22
 0:09:47
0:09:47
 1:17:15
1:17:15
 0:05:00
0:05:00
 0:11:11
0:11:11
 0:13:00
0:13:00