filmov
tv
Nmap - HTTP Enumeration - Detecting HTTP Methods

Показать описание
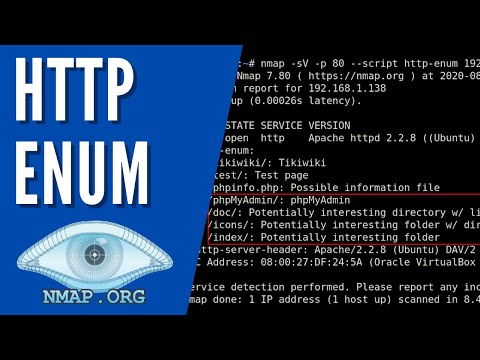
In this video, I demonstrate how to detect the active HTTP methods on a web server with Nmap. Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection.
� SUPPORT US:
SOCIAL NETWORKS:
WHERE YOU CAN FIND US ONLINE:
LISTEN TO THE CYBERTALK PODCAST:
We hope you enjoyed the video and found value in the content. We value your feedback. If you have any questions or suggestions feel free to post them in the comments section or contact us directly via our social platforms.
Thanks for watching!
Благодарю за просмотр!
Kiitos katsomisesta
Danke fürs Zuschauen!
感谢您观看
Merci d'avoir regardé
Obrigado por assistir
دیکھنے کے لیے شکریہ
देखने के लिए धन्यवाद
Grazie per la visione
Gracias por ver
شكرا للمشاهدة
#Nmap
� SUPPORT US:
SOCIAL NETWORKS:
WHERE YOU CAN FIND US ONLINE:
LISTEN TO THE CYBERTALK PODCAST:
We hope you enjoyed the video and found value in the content. We value your feedback. If you have any questions or suggestions feel free to post them in the comments section or contact us directly via our social platforms.
Thanks for watching!
Благодарю за просмотр!
Kiitos katsomisesta
Danke fürs Zuschauen!
感谢您观看
Merci d'avoir regardé
Obrigado por assistir
دیکھنے کے لیے شکریہ
देखने के लिए धन्यवाद
Grazie per la visione
Gracias por ver
شكرا للمشاهدة
#Nmap
Nmap - HTTP Enumeration - Detecting HTTP Methods
Nmap - HTTP Enumeration - Finding Hidden Files And Directories
Nmap - HTTP Enumeration - WAF Detection And Fingerprinting
HTTP Enumeration with Nmap
Nmap - HTTP Enumeration |
Nmap Tutorial to find Network Vulnerabilities
10 NMAP HTTP Enumeration
NMAP Basic - Web Directory Enumeration [ nmap http-enum ] #nmap #metasploit #ethicalhacking
Nmap Http directory enumeration
HTTP Enum (Find Hidden Files and directories) Using Nmap // Episode 9
HTTP Method Enumeration using Nmap and Metasploit
NMAP Tutorial for Beginners! Network Attacks
Nmap exploit - http-domino-enum-passwords.nse
Introduction To The Nmap Scripting Engine (NSE)
How HACKERS find Network Vulnerabilities (with Nmap Scripts)
Scan & Enumeration with Kali Linux:Choos Target with nmap & Determin If It Is Viable|packtpu...
Network Enumeration Techniques with Nmap | SMB, FTP, SNMP, HTTP, DNS, SSH & More Explained
Introduction To Pentesting - Enumeration
system hacking || telnet enumeration || nmap || #systemhacking #hacking #cybersecurity #nmap
44 Fingerprinting and Enumeration with nmap
Scan & Enumeration with Kali Linux: Choosing a Target with nmap | packtpub.com
How Hackers Scan Devices on a Network with Nmap | Kali Linux
Mastering Nmap : Remote Enumeration and Exploitation | packtpub.com
Uncover Web Server Details with Nmap NSE | Powerful Web Enumeration Techniques!
Комментарии
 0:07:08
0:07:08
 0:08:04
0:08:04
 0:10:08
0:10:08
 0:09:24
0:09:24
 0:09:19
0:09:19
 0:17:09
0:17:09
 0:02:53
0:02:53
 0:00:25
0:00:25
 0:02:55
0:02:55
 0:06:55
0:06:55
 0:01:48
0:01:48
 0:15:51
0:15:51
 0:02:30
0:02:30
 0:06:45
0:06:45
 0:04:29
0:04:29
 0:05:40
0:05:40
 0:57:48
0:57:48
 0:39:22
0:39:22
 0:00:16
0:00:16
 0:09:47
0:09:47
 0:06:46
0:06:46
 0:05:27
0:05:27
 0:08:03
0:08:03
 0:06:31
0:06:31