filmov
tv
55 SQL Injection Database User priviliges Writing Files secure file priv creating a backdoor Part 1

Показать описание
Writing files
When it comes to writing files to the back-end server, it becomes much more limited in modern DBMS systems, as we can use this to write a web shell on the remote server, and hence get code execution and take over the server. This is why modern DBMS systems disable file writing by default and require certain permissions for DBA's to write files. Before writing files, we must first check if we have enough rights and if the DBMS allows writing files.
Write permissions to the file
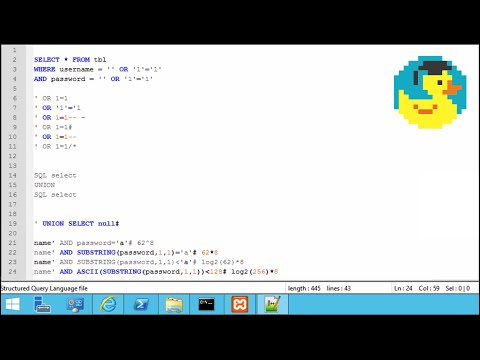
To be able to write files to the backend using a MySQL database, we require three things:
User with FILE permission enabled
MySQL global variable secure_file_priv is not enabled
Write permission to the place we want to write to on the backend server
We have already discovered that our current user has the necessary FILE permission to write files. Now we need to check if the MySQL database has this permission. This can be done by checking the secure_file_priv global variable.
secure_file_priv
The secure_file_priv variable is used to determine where to read/write files from. An empty value allows us to read files from the entire file system. Otherwise, if a specific directory is specified, we can only read from the folder specified by the variable. On the other hand, NULL means we cannot read/write from any directory. MariaDB has this variable set to empty by default, which allows us to read/write to any file if the user has FILE permission.
However, MySQL uses var/lib/mysql-files/ as the default folder.
This means that reading files using MySQL injection is not possible with the default settings. Even worse, some modern configurations default to NULL, meaning we can't read/write files anywhere on the system.
So let's see how we can find out the value of secure_file_priv. Within MySQL, we can use the following query to get the value of this variable:
SHOW VARIABLES LIKE 'secure_file_priv';
'secure_file_priv', '/var/lib/mysql-files/'
SELECT INTO OUTFILE
Now that we've confirmed that our user needs to write files to the backend, let's try doing that using the SELECT .. INTO OUTFILE statement. The SELECT INTO OUTFILE statement can be used to write data from selected queries to files. This is commonly used to export data from tables.
To use it, we can add INTO OUTFILE '...' after our query to export the results to the file we specified. The example below saves the output of the user table in the /tmp/credentials file:
SELECT * from logins INTO OUTFILE '/tmp/credentials';
If we go to the back-end server and display the file, we will see the contents of the table:
cat /tmp/credentials
Writing a Web Shell
================
Once the write permissions are approved, we can proceed to write a PHP web shell to the webroot folder. We can write the following PHP webshell to be able to execute commands directly on the backend server:
php system($_REQUEST[0]);
When it comes to writing files to the back-end server, it becomes much more limited in modern DBMS systems, as we can use this to write a web shell on the remote server, and hence get code execution and take over the server. This is why modern DBMS systems disable file writing by default and require certain permissions for DBA's to write files. Before writing files, we must first check if we have enough rights and if the DBMS allows writing files.
Write permissions to the file
To be able to write files to the backend using a MySQL database, we require three things:
User with FILE permission enabled
MySQL global variable secure_file_priv is not enabled
Write permission to the place we want to write to on the backend server
We have already discovered that our current user has the necessary FILE permission to write files. Now we need to check if the MySQL database has this permission. This can be done by checking the secure_file_priv global variable.
secure_file_priv
The secure_file_priv variable is used to determine where to read/write files from. An empty value allows us to read files from the entire file system. Otherwise, if a specific directory is specified, we can only read from the folder specified by the variable. On the other hand, NULL means we cannot read/write from any directory. MariaDB has this variable set to empty by default, which allows us to read/write to any file if the user has FILE permission.
However, MySQL uses var/lib/mysql-files/ as the default folder.
This means that reading files using MySQL injection is not possible with the default settings. Even worse, some modern configurations default to NULL, meaning we can't read/write files anywhere on the system.
So let's see how we can find out the value of secure_file_priv. Within MySQL, we can use the following query to get the value of this variable:
SHOW VARIABLES LIKE 'secure_file_priv';
'secure_file_priv', '/var/lib/mysql-files/'
SELECT INTO OUTFILE
Now that we've confirmed that our user needs to write files to the backend, let's try doing that using the SELECT .. INTO OUTFILE statement. The SELECT INTO OUTFILE statement can be used to write data from selected queries to files. This is commonly used to export data from tables.
To use it, we can add INTO OUTFILE '...' after our query to export the results to the file we specified. The example below saves the output of the user table in the /tmp/credentials file:
SELECT * from logins INTO OUTFILE '/tmp/credentials';
If we go to the back-end server and display the file, we will see the contents of the table:
cat /tmp/credentials
Writing a Web Shell
================
Once the write permissions are approved, we can proceed to write a PHP web shell to the webroot folder. We can write the following PHP webshell to be able to execute commands directly on the backend server:
php system($_REQUEST[0]);
 0:05:04
0:05:04
 0:11:31
0:11:31
 0:04:55
0:04:55
 0:02:39
0:02:39
 0:32:54
0:32:54
 0:00:55
0:00:55
 0:09:18
0:09:18
 0:17:57
0:17:57
 0:02:23
0:02:23
 0:46:35
0:46:35
 0:52:52
0:52:52
 0:07:13
0:07:13
 0:23:18
0:23:18
 0:01:00
0:01:00
 0:00:16
0:00:16
 0:17:52
0:17:52
 0:45:36
0:45:36
 0:04:08
0:04:08
 0:05:59
0:05:59
 0:21:21
0:21:21
 0:27:45
0:27:45
 0:00:56
0:00:56
 0:04:29
0:04:29
 0:46:49
0:46:49