filmov
tv
JWT - JSON Web Token Crash Course (NodeJS & Postgres)

Показать описание
JSON Web Token (JWT, sometimes pronounced JOT) an internet standard for creating JSON-based access tokens that assert some number of claims. The tokens are signed either using a private secret or a public/private key.
In this video I want to discuss the difference between JWT (JSON web Tokens) and Session-Based Authentication. I will show examples with Node JS and Postgres. Finally, I’ll discuss the pros and cons of JWT.
Chapters
0:00 Intro
2:25 Session-Based Auth
9:00 JWT Based Auth
16:10 Refresh Tokens
25:17 Asymmetric JWT
28:16 Example coding
42:00 Pros and Cons
Source Code
Resources
draft-ietf-oauth-jwt-bcp-07 - JSON Web Token Best Current Practices
🏭 Software Architecture Videos
💾 Database Engineering Videos
🛰 Network Engineering Videos
🏰 Load Balancing and Proxies Videos
🐘 Postgres Videos
🚢Docker
🧮 Programming Pattern Videos
🛡 Web Security Videos
🦠 HTTP Videos
🐍 Python Videos
🔆 Javascript Videos
Support me on PayPal
Become a Patreon
Stay Awesome,
Hussein
In this video I want to discuss the difference between JWT (JSON web Tokens) and Session-Based Authentication. I will show examples with Node JS and Postgres. Finally, I’ll discuss the pros and cons of JWT.
Chapters
0:00 Intro
2:25 Session-Based Auth
9:00 JWT Based Auth
16:10 Refresh Tokens
25:17 Asymmetric JWT
28:16 Example coding
42:00 Pros and Cons
Source Code
Resources
draft-ietf-oauth-jwt-bcp-07 - JSON Web Token Best Current Practices
🏭 Software Architecture Videos
💾 Database Engineering Videos
🛰 Network Engineering Videos
🏰 Load Balancing and Proxies Videos
🐘 Postgres Videos
🚢Docker
🧮 Programming Pattern Videos
🛡 Web Security Videos
🦠 HTTP Videos
🐍 Python Videos
🔆 Javascript Videos
Support me on PayPal
Become a Patreon
Stay Awesome,
Hussein
Комментарии
 0:02:18
0:02:18
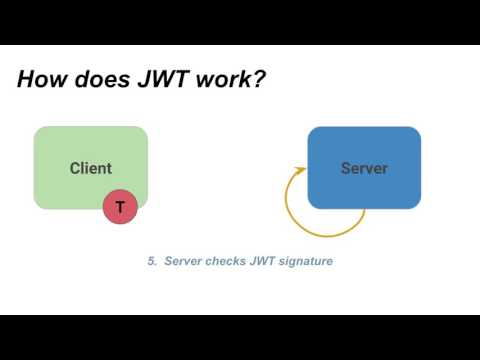 0:01:07
0:01:07
 0:05:13
0:05:13
 0:14:53
0:14:53
 0:05:14
0:05:14
 0:14:53
0:14:53
 0:07:00
0:07:00
 0:11:24
0:11:24
 0:19:07
0:19:07
 0:27:36
0:27:36
 0:14:47
0:14:47
 0:11:27
0:11:27
 0:10:20
0:10:20
 0:14:32
0:14:32
 0:06:30
0:06:30
 0:10:25
0:10:25
 0:09:18
0:09:18
 0:26:12
0:26:12
 0:14:34
0:14:34
 0:10:07
0:10:07
 0:10:09
0:10:09
 0:11:53
0:11:53
 0:08:25
0:08:25
 1:41:00
1:41:00