filmov
tv
ORCA ransomware removal instructions [Zeppelin family].

Показать описание
Note that Combo Cleaner Antivirus does not decrypt files initially encrypted by ransomware. It helps to remove the ransomware-type infection and protects your data from ransomware attacks in the future, however, it does not decrypt the files already damaged by the ransomware.
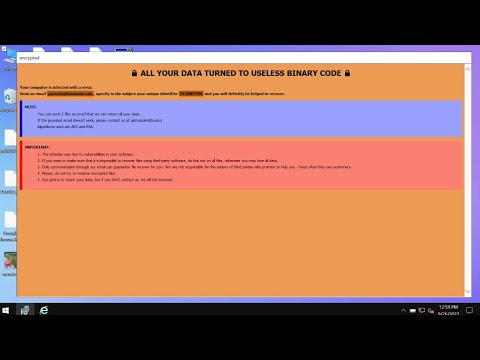
Quotation from the ransom note:
QUOTE
YOUR FILES HAVE BEEN ENCRYPTED
Your ID to decrypt: 1A2-FD3-318
Unfortunately for you, due to a serious vulnerability in IT security, you are vulnerable to attacks!
To decrypt files, you need to get a private key.
The only copy of the secret key that can be used to decrypt files is on a private server.
The server will destroy the key within 72h after the encryption is completed.
To save the key for a longer period, you can contact us and provide your ID!
In addition, we collect strictly confidential/personal data.
This data is also stored on a private server.
Your data will be deleted only after payment!
If you decide not to pay, we will publish your data to everyone or resellers.
So you can expect your data to become publicly available in the near future!
It's just a business and we only care about making a profit!
The only way to get your files back is to contact us for further instructions!
To establish a trust relationship, you can send 1 file for test decryption (no more than 5 MB)
⇓ ⇓ ⇓ ⇓ ⇓ ⇓ ⇓ ⇓
Do not waste your time searching for other decryption methods - THERE ARE NONE, you will pay more for your time!
Every day the price of decryption increases!
Do not rename encrypted files.
Do not use third-party programs to decrypt files - they can only do harm!
After payment, you get a decoder (.exe), you only need to run it, and it will do everything by itself.
I only accept Bitcoins! You can learn how to buy them on the Internet.
UNQUOTE
Quotation from the ransom note:
QUOTE
YOUR FILES HAVE BEEN ENCRYPTED
Your ID to decrypt: 1A2-FD3-318
Unfortunately for you, due to a serious vulnerability in IT security, you are vulnerable to attacks!
To decrypt files, you need to get a private key.
The only copy of the secret key that can be used to decrypt files is on a private server.
The server will destroy the key within 72h after the encryption is completed.
To save the key for a longer period, you can contact us and provide your ID!
In addition, we collect strictly confidential/personal data.
This data is also stored on a private server.
Your data will be deleted only after payment!
If you decide not to pay, we will publish your data to everyone or resellers.
So you can expect your data to become publicly available in the near future!
It's just a business and we only care about making a profit!
The only way to get your files back is to contact us for further instructions!
To establish a trust relationship, you can send 1 file for test decryption (no more than 5 MB)
⇓ ⇓ ⇓ ⇓ ⇓ ⇓ ⇓ ⇓
Do not waste your time searching for other decryption methods - THERE ARE NONE, you will pay more for your time!
Every day the price of decryption increases!
Do not rename encrypted files.
Do not use third-party programs to decrypt files - they can only do harm!
After payment, you get a decoder (.exe), you only need to run it, and it will do everything by itself.
I only accept Bitcoins! You can learn how to buy them on the Internet.
UNQUOTE
 0:03:12
0:03:12
 0:04:00
0:04:00
 0:03:42
0:03:42
 0:03:26
0:03:26
 0:03:57
0:03:57
 0:04:57
0:04:57
 0:03:03
0:03:03
 0:01:35
0:01:35
 0:04:26
0:04:26
 0:03:56
0:03:56
 0:02:58
0:02:58
 0:09:50
0:09:50
 0:07:04
0:07:04
 0:01:01
0:01:01
 0:02:15
0:02:15
 0:02:38
0:02:38
 0:03:51
0:03:51
 0:03:50
0:03:50
 0:03:29
0:03:29
 0:02:29
0:02:29
 0:02:29
0:02:29
 0:48:19
0:48:19
 0:58:45
0:58:45