filmov
tv
Identity Provider SSO vs Service Provider SSO: What's the Difference?

Показать описание
Resources and social media:
#jumpcloud #singlesignon #identitymanagement
Transcript:
Tired of juggling multiple passwords for different applications every day? Say goodbye to password overload and hello to Single Sign-On, or SSO!
Now, when it comes to implementing SSO, there are two methods you should know about. The first one is IdP-Initiated SSO, and the second is SP-Initiated SSO.
Let's dive right in and understand what each one means and how they differ.
The main difference between the two methods lies in where you start the login process. With IdP-Initiated SSO, you begin at the identity provider, while with SP-Initiated SSO, you start at the application you want to access.
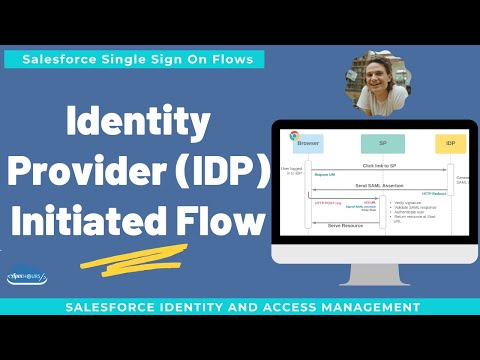
Here's how IdP-Initiated SSO works.
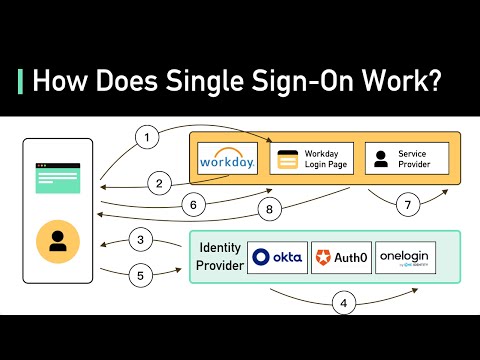
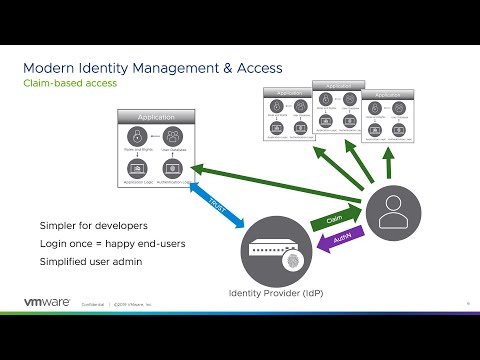
When you want to access an application, you go to your company's identity provider. It could be a system like OpenLDAP, Microsoft Active Directory, or a cloud-based IdP like JumpCloud.
Once you're on the identity provider's platform, you simply click on the application you want to access.
Behind the scenes, the identity provider sends a request to the service provider, verifying your access privileges.
And if the service provider accepts the request, you're granted access to the application, and you can start your session.
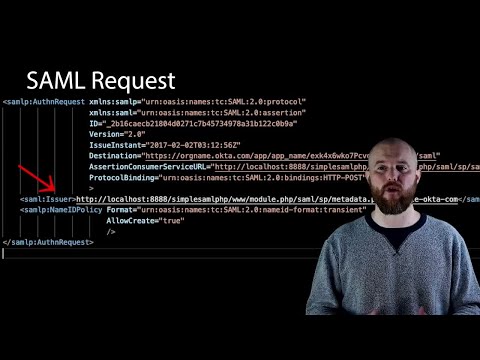
With SP-Initiated SSO, however, the login process starts at the service provider.
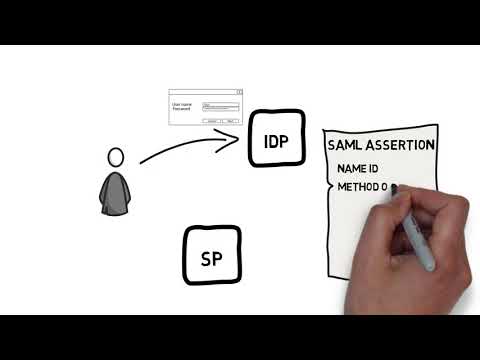
Imagine you want to log into an application. Instead of going to the identity provider first, you start at the application's login page.
Once you enter your credentials, the application redirects you to your company's identity provider for authentication.
The identity provider verifies your identity and access level, and then sends a response back to the service provider, granting you access to the application.
Now that we understand both methods, let's compare the advantages and disadvantages of each.
IdP-Initiated SSO offers more flexibility and is essential when certain service providers can't issue SAML requests.
However, it is susceptible to man-in-the-middle attacks and can sometimes overwrite existing sessions within a service provider.
On the other hand, SP-Initiated SSO allows users to initiate their login directly from the application, but it may be more challenging to troubleshoot if errors occur.
To mitigate the risk of man-in-the-middle attacks in IdP-Initiated SSO, there are three things you can do.
First, configure your identity provider to use the minimum possible response trust length. This minimizes the time for interception and ensures greater security.
Second, implement replay detection to prevent unauthorized access through reused SAML assertions.
Lastly, make sure that service providers in your IdP-initiated SSO workflow do not accept unsolicited SAML responses. This helps protect against SAML theft.
So, which method among the two is better?
When implementing SSO, it's important to choose a reliable SSO provider that offers additional security controls and identity and access management capabilities.
This is where JumpCloud comes in. It's an ideal solution for modern enterprises, connecting users securely to various resources regardless of location, platform, or provider.
JumpCloud supports popular applications like Salesforce, Atlassian, Google Workspace, and file storage providers like Google Drive and Dropbox, among others.
To see it in action, click the link in the description to try JumpCloud’s SSO for free.
Комментарии
 0:03:34
0:03:34
 0:04:54
0:04:54
 0:15:35
0:15:35
 0:01:25
0:01:25
 1:01:38
1:01:38
 0:02:35
0:02:35
 0:06:24
0:06:24
 0:04:33
0:04:33
 0:07:11
0:07:11
 0:06:06
0:06:06
 0:05:18
0:05:18
 0:11:49
0:11:49
 0:02:49
0:02:49
 0:03:14
0:03:14
 0:03:00
0:03:00
 0:09:52
0:09:52
 0:07:23
0:07:23
 0:15:22
0:15:22
 0:08:38
0:08:38
 0:06:19
0:06:19
 0:27:47
0:27:47
 0:10:01
0:10:01
 0:15:30
0:15:30
 0:17:53
0:17:53