filmov
tv
How to Configure AAA, TACACS and RADIUS (Step by Step)
Показать описание
TIMESTAMPS:
0:00 Introduction
3:40 Configuring Authentication
15:50 Testing if SSH works as expected
19:48 Authentication Configuration Using TACACS+
22:10 Simulation if TACACS+/RADIUS Server is Down
27:48 SSH into R2 from PC2
28:48 Console into S1 from PC1
29:36 Conclusion
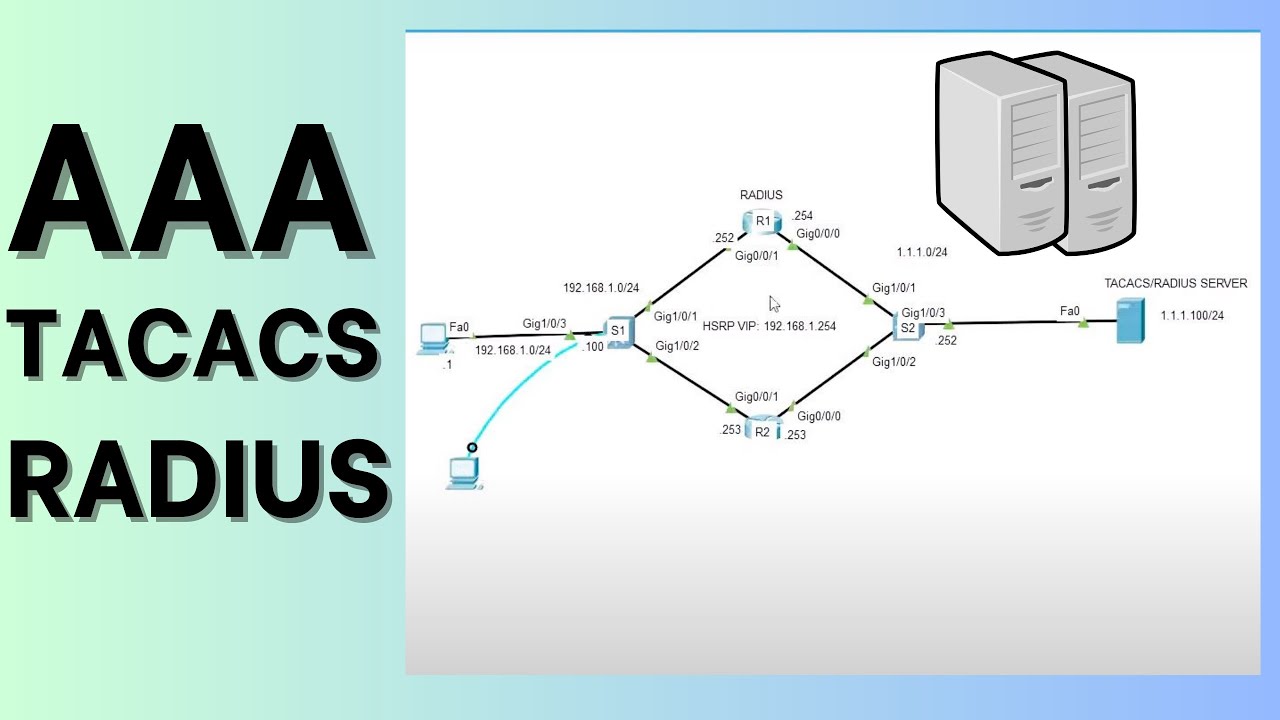
In a nutshell, you can think of AAA in the following manner:
Authentication: Who is the user?
Authorization: What is the user allowed to do?
Accounting: What did the user do?
User authentication can be handled by several methods:
1. Usernames and passwords configured locally on the devices username cisco secret cisco
2. One or more external Remote Authentication Dial-In User Service (RADIUS) servers
3. One or more external Terminal Access Controller Access Control System+ (TACACS+) servers
Configuring Authentication:
Step 1: Enable AAA on the switch.
aaa new-model
Step 2: Define the source of authentication.
username cisco secret cisco
tacacs-server host 1.1.1.100 key cisco
Step 3: Define a list of authentication methods to try.
aaa authentication login default group tacacs+ local
aaa authentication enable default group tacacs+ local
Step 4: Apply a method list to a switch line.
line vty 0 15
login authentication default
Step 5: After authentication is configured on a device, it is a good idea to stay logged
in on one session so that the authentication can be tested. If you exit the configuration
session, you will not be able to log in again if the authentication is
misconfigured. While you stay logged in on the original session, bring up a
new SSH session to the switch. If you can authenticate successfully, everything
is configured properly.
Tip: Be sure to add either the local or line methods at the end of the list, as a last resort.
This way, if all the RADIUS or TACACS+ servers are unavailable or the switch is completely
isolated from the rest of the network, a locally configured authentication method will
eventually be used. Otherwise, you will never be able to access the device until at least one
of the servers comes back online.
Reference: CCNP Routing and Switching SWITCH 300-115 Official Cert Guide
David Hucaby, CCIE No. 4594
#cisco #ccna #ccnp #ccie
0:00 Introduction
3:40 Configuring Authentication
15:50 Testing if SSH works as expected
19:48 Authentication Configuration Using TACACS+
22:10 Simulation if TACACS+/RADIUS Server is Down
27:48 SSH into R2 from PC2
28:48 Console into S1 from PC1
29:36 Conclusion
In a nutshell, you can think of AAA in the following manner:
Authentication: Who is the user?
Authorization: What is the user allowed to do?
Accounting: What did the user do?
User authentication can be handled by several methods:
1. Usernames and passwords configured locally on the devices username cisco secret cisco
2. One or more external Remote Authentication Dial-In User Service (RADIUS) servers
3. One or more external Terminal Access Controller Access Control System+ (TACACS+) servers
Configuring Authentication:
Step 1: Enable AAA on the switch.
aaa new-model
Step 2: Define the source of authentication.
username cisco secret cisco
tacacs-server host 1.1.1.100 key cisco
Step 3: Define a list of authentication methods to try.
aaa authentication login default group tacacs+ local
aaa authentication enable default group tacacs+ local
Step 4: Apply a method list to a switch line.
line vty 0 15
login authentication default
Step 5: After authentication is configured on a device, it is a good idea to stay logged
in on one session so that the authentication can be tested. If you exit the configuration
session, you will not be able to log in again if the authentication is
misconfigured. While you stay logged in on the original session, bring up a
new SSH session to the switch. If you can authenticate successfully, everything
is configured properly.
Tip: Be sure to add either the local or line methods at the end of the list, as a last resort.
This way, if all the RADIUS or TACACS+ servers are unavailable or the switch is completely
isolated from the rest of the network, a locally configured authentication method will
eventually be used. Otherwise, you will never be able to access the device until at least one
of the servers comes back online.
Reference: CCNP Routing and Switching SWITCH 300-115 Official Cert Guide
David Hucaby, CCIE No. 4594
#cisco #ccna #ccnp #ccie
Комментарии
 0:12:53
0:12:53
 0:07:19
0:07:19
 0:05:00
0:05:00
 0:10:17
0:10:17
 0:29:46
0:29:46
 0:05:19
0:05:19
 0:10:15
0:10:15
 0:06:10
0:06:10
 0:19:10
0:19:10
 0:05:13
0:05:13
 0:02:01
0:02:01
 0:10:06
0:10:06
 0:05:37
0:05:37
 0:13:57
0:13:57
 0:12:09
0:12:09
 0:11:21
0:11:21
 0:20:33
0:20:33
 0:03:05
0:03:05
 0:01:01
0:01:01
 0:14:01
0:14:01
 0:07:45
0:07:45
 0:05:49
0:05:49
 1:06:18
1:06:18
 0:04:39
0:04:39