filmov
tv
AUTOSAR | CYBER SECURITY | FUNDAMETALS OF CYBER SECURITY | BASIC OVERVIEW

Показать описание
This is Basic Overview of Cyber Security Stack and the key concepts used in it. It will give you the overview of working principle of Cyber Security Stack.
AUTOSAR | CYBER SECURITY | FUNDAMETALS OF CYBER SECURITY | BASIC OVERVIEW
Automotive Cybersecurity - Over simplified
AUTOSAR SecOC Part-1 | Secure On-board Communication | AUTOSAR | AUTOMOTIVE Embedded
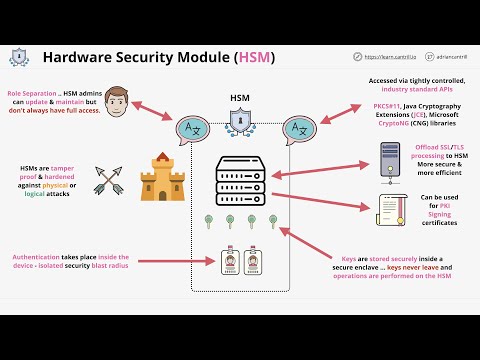
What are hardware security modules (HSM), why we need them and how they work.
Master SecOC in practice - Learn to know the three major operational challenges
An AUTOSAR based Solution for Automotive IDS
AUTOSAR Intrusion Detection System Manager - MICROSAR IdsM
With AUTOSAR to UNECE-compliant cybersecurity
Certificate-Based Authentication in Vehicle Diagnostics #1: What is Possible in UDS and AUTOSAR?
AUTOSAR Basics | AUTOSAR Tutorial | Architecture | Automotive
What is Crypto Module In Automotive/What is need of cyber security in Automotive
What is Secure Boot in embedded || Cryptography || Security || IoT || Automotive?
Flash Boot Loader : Basics | Automotive | AUTOSAR
Automotive Devices Security Architecture
Introduction to Automotive Embedded Cybersecurity
Webinar: Security on communication stack
Automotive hacking: Remotely hacking into a brand new car | Upstream Security
Cybersecurity in Automotive Part1 (2019)
Securing modern vehicles with AUTOSAR
#VTT19 On the Spot: Hardware Security Modules and Automotive Cybersecurity
Software Update Management System (SUMS) | Automotive Cybersecurity
The Problem with 2nd Gen Cybersecurity Vehicles
AUTOSAR Adaptive Platform - Safety and Security - Rinat Asmus (2019)
Episode 4 is out now! | Learn CLASSIC AUTOSAR
Комментарии
 0:02:21
0:02:21
 0:05:43
0:05:43
 0:06:40
0:06:40
 0:13:14
0:13:14
 0:56:54
0:56:54
 0:10:51
0:10:51
 0:52:55
0:52:55
 0:19:31
0:19:31
 0:08:47
0:08:47
 0:03:24
0:03:24
 0:01:29
0:01:29
 0:10:24
0:10:24
 0:26:53
0:26:53
 1:19:26
1:19:26
 1:18:51
1:18:51
 0:07:06
0:07:06
 0:35:33
0:35:33
 0:45:15
0:45:15
 0:03:30
0:03:30
 0:16:50
0:16:50
 0:00:48
0:00:48
 0:35:47
0:35:47
 0:00:23
0:00:23