filmov
tv
Secure logging with syslog-ng Forward integrity and confidentiality of system logs

Показать описание
by Stephan Marwedel
At: FOSDEM 2020
The design, implementation, and configuration of the secure logging service. Its aim is to provide tamper evident logging, i.e., to adequately protect log records of an information system against tampering and to provide a sensor indicating attack attempts. The secure logging service achieves this by authentically encrypting each log record with an individual cryptographic key used only once and protects integrity of the whole log archive by a cipher{based message authentication
code. Each attempt to tamper with either an individual log record or the log archive itself will be immediately detected during log archive verification. Therefore, an attacker can no longer tamper with log records without being detected which greatly enhances the use of log archives in forensic investigations.
Log records are normally produced by any information system in order to perform monitoring during normal operations and for troubleshooting in case of technical problems. Log information is equally important for retaining the security of an information system, as security relevant events are recorded and can later be monitored for unusual patterns which may indicate an attack attempt. Examples include log on and log off, startup and shutdown, network service access, network filter rule application, storage access, etc. Log records may also contain valuable information about a system that a potential attacker intends to compromise. If an attacker is able to successfully compromise a system, they are also able to tamper with log records, potentially hiding their traces. This makes forensic analysis extremely difficult, as no reliable data source about system behavior immediately before the attack is available to a security analyst performing incident investigation. Therefore, log information should be appropriately protected. The aim of the secure logging service is to provide tamper evident logging, i.e., to adequately protect log records of an information system and to provide a sensor indicating attack attempts. The secure logging service achieves this by authentically encrypting each log record with an individual cryptographic key used only once and protects integrity of the whole log archive by a cryptographic authentication code. Each attempt to tamper with either an individual log record or the log archive itself will be immediately detected during log archive verification. Therefore, an attacker can no longer tamper with log records
without being detected. ost information systems rely on standards in order to provide logging services. One of the most widely adopted standards is the syslog protocol which is specified in RFC 5424. Many implementations of this
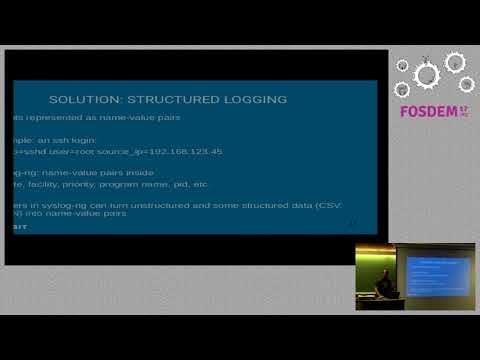
protocol are available. A popular extensible implementation with additional features is syslog-ng, which is an enhanced logging daemon with advanced features for input and output. Furthermore, it features capabilities for log message filtering, rewriting, and routing. It can be used as a drop-in replacement for existing log daemons on UNIX systems. The implementation of the secure logging service providing tamper evidence and confidentiality of system logs based on the template mechanism of syslog-ng is presented together with an application example.
Room: UA2.114 (Baudoux)
Scheduled start: 2020-02-01 13:30:00
At: FOSDEM 2020
The design, implementation, and configuration of the secure logging service. Its aim is to provide tamper evident logging, i.e., to adequately protect log records of an information system against tampering and to provide a sensor indicating attack attempts. The secure logging service achieves this by authentically encrypting each log record with an individual cryptographic key used only once and protects integrity of the whole log archive by a cipher{based message authentication
code. Each attempt to tamper with either an individual log record or the log archive itself will be immediately detected during log archive verification. Therefore, an attacker can no longer tamper with log records without being detected which greatly enhances the use of log archives in forensic investigations.
Log records are normally produced by any information system in order to perform monitoring during normal operations and for troubleshooting in case of technical problems. Log information is equally important for retaining the security of an information system, as security relevant events are recorded and can later be monitored for unusual patterns which may indicate an attack attempt. Examples include log on and log off, startup and shutdown, network service access, network filter rule application, storage access, etc. Log records may also contain valuable information about a system that a potential attacker intends to compromise. If an attacker is able to successfully compromise a system, they are also able to tamper with log records, potentially hiding their traces. This makes forensic analysis extremely difficult, as no reliable data source about system behavior immediately before the attack is available to a security analyst performing incident investigation. Therefore, log information should be appropriately protected. The aim of the secure logging service is to provide tamper evident logging, i.e., to adequately protect log records of an information system and to provide a sensor indicating attack attempts. The secure logging service achieves this by authentically encrypting each log record with an individual cryptographic key used only once and protects integrity of the whole log archive by a cryptographic authentication code. Each attempt to tamper with either an individual log record or the log archive itself will be immediately detected during log archive verification. Therefore, an attacker can no longer tamper with log records
without being detected. ost information systems rely on standards in order to provide logging services. One of the most widely adopted standards is the syslog protocol which is specified in RFC 5424. Many implementations of this
protocol are available. A popular extensible implementation with additional features is syslog-ng, which is an enhanced logging daemon with advanced features for input and output. Furthermore, it features capabilities for log message filtering, rewriting, and routing. It can be used as a drop-in replacement for existing log daemons on UNIX systems. The implementation of the secure logging service providing tamper evidence and confidentiality of system logs based on the template mechanism of syslog-ng is presented together with an application example.
Room: UA2.114 (Baudoux)
Scheduled start: 2020-02-01 13:30:00
 0:25:35
0:25:35
 0:25:35
0:25:35
 0:23:51
0:23:51
 0:03:07
0:03:07
 0:02:31
0:02:31
 0:01:21
0:01:21
 0:02:22
0:02:22
 0:05:33
0:05:33
 0:02:36
0:02:36
 0:02:17
0:02:17
 0:02:39
0:02:39
 0:23:51
0:23:51
 0:02:36
0:02:36
 0:02:38
0:02:38
 0:29:53
0:29:53
 0:12:50
0:12:50
![[Paloalto Firewall] log](https://i.ytimg.com/vi/0PNrXWhpEiE/hqdefault.jpg) 0:13:47
0:13:47
 0:02:39
0:02:39
 0:01:58
0:01:58
 0:11:17
0:11:17
 0:19:59
0:19:59
 0:03:00
0:03:00
 0:16:49
0:16:49
 0:08:43
0:08:43