filmov
tv
Understanding Fortinet's Legacy of Security Flaws From Magic Back Door to XORtigate CVE-2023-27997

Показать описание
Volt Typhoon
Connecting With Us
---------------------------------------------------
Lawrence Systems Shirts and Swag
---------------------------------------------------
AFFILIATES & REFERRAL LINKS
---------------------------------------------------
Amazon Affiliate Store
UniFi Affiliate Link
All Of Our Affiliates that help us out and can get you discounts!
Gear we use on Kit
Use OfferCode LTSERVICES to get 10% off your order at
Digital Ocean Offer Code
HostiFi UniFi Cloud Hosting Service
Protect you privacy with a VPN from Private Internet Access
Patreon
⏱️ Time Stamps ⏱️
00:00 Fortinet Security
01:10 Fortinet Magic String
02:22 Volt Typhoon
03:14 XORtigate Fortigate VPN CVE-2023-27997
#firewall #fortinet #security
Understanding Fortinet's Legacy of Security Flaws From Magic Back Door to XORtigate CVE-2023-27...
A New Approach to Cybersecurity | The Fortinet Security Fabric
What Is Firewall ? | Firewall Explained | Firewalls and Network Security | Simplilearn
Fortinet CVE 2022 40864 Explained
Fortinet Security Driven Networking in 2021
How Fortinet’s Security Fabric Delivers Agile Cloud Security
Fortinet Advanced Threat Protection (ATP) Framework
Fortinet | Background & History
Overview of Fortinet Universal SASE
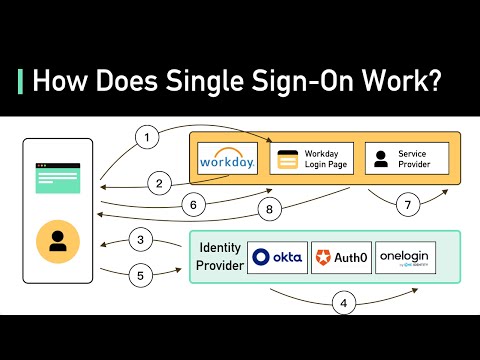
What Is Single Sign-on (SSO)? How It Works
Fortinet Runs Next Gen Firewall via FastConnect, Exadata on OCI
What Is SIEM?
ALERT: Critical Vulnerability on FortiGate and FortiProxy
FortiGate Security Antivirus
Introducing the FortiGate Rugged 70F | Next-Generation Firewall
What Is IAM? | Identity and Access Management for Beginners (IAM) | IAM for Beginners | Simplilearn
Welcome to FortiGate Cloud | Fortinet
Connecting OT/IoT into Security Fabric - TGIF Webinar Fortinet and Nozomi Networks
Next-Gen Wi-Fi Security - WPA3 Explained
What is SD-WAN?
CompTIA Security+ Full Course: Application Protocol Security
Introducing Operational Technology - Securing Your Industrial Customers - Fortinet webinar
FortiGate Firewall Crash Course [PART 1] | Practical Based
The Solution to Legacy Endpoint Protection: Leveraging FortiEDR to Ease Customer Pain Points Webinar
Комментарии
 0:07:35
0:07:35
 0:01:22
0:01:22
 0:05:39
0:05:39
 0:02:11
0:02:11
 0:15:33
0:15:33
 0:20:15
0:20:15
 0:01:09
0:01:09
 0:06:54
0:06:54
 0:19:06
0:19:06
 0:04:54
0:04:54
 0:08:35
0:08:35
 0:04:29
0:04:29
 0:02:44
0:02:44
 0:23:04
0:23:04
 0:02:14
0:02:14
 0:09:11
0:09:11
 0:04:30
0:04:30
 0:58:02
0:58:02
 0:05:26
0:05:26
 0:01:33
0:01:33
 0:42:53
0:42:53
 0:44:38
0:44:38
 1:25:41
1:25:41
 0:29:17
0:29:17