filmov
tv
Wireshark and Recognizing Exploits, HakTip 138

Показать описание
Hak5 -- Cyber Security Education, Inspiration, News & Community since 2005:
____________________________________________
This week on HakTip, Shannon pinpoints an exploitation using Wireshark.
Working on the shoulders of last week's episode, this week we'll discuss what exploits look like in Wireshark. The example I'm sharing is from Practical Packet Analysis, a book by Chris Sanders about Wireshark.
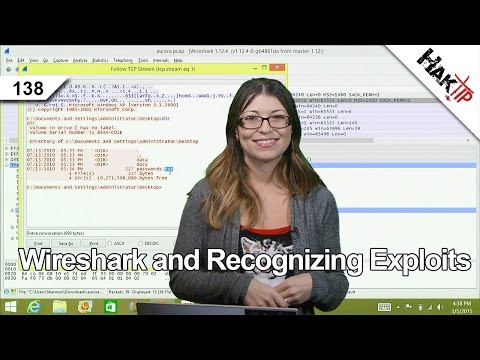
Our example packet shows what happens when a user visits a malicious site using a bad version of IE. This is called spear phishing. First, we have HTTP traffic on port 80. We notice there is a 302 moved response from the malicious site and the location is all sorts of weird. Then a bunch of data gets transferred from the new site to the user. Click Follow TCP Stream. If you scroll down, you see some weird gibberish that doesn't make sense and an iframe script. In this case, it's the exploit being sent to the user.
Scroll down to packet 21 and take a look at the .gif GET request. Lastly, Follow packet 25's TCP Stream. This shows us a windows command shell, and the attacker gaining admin priveledges to view our user's files. FREAKY. But now a network admin could use their intrusion detection system to set up a new alarm whenever an attack of this nature is seen.
If someone is trying to do a MITM attack on a user, it might look like our next example packet. 54 and 55 are just ARP packets being sent back and forth, but in packet 56 the attacker sends another ARP packet with a different MAC address for the router, thereby sending the user's data to the attacker then to the router. Compare 57 to 40, and you see the same IP address, but different macs for the destination. This is ARP cache Poisoning.
-~-~~-~~~-~~-~-
Please watch: "Bash Bunny Primer - Hak5 2225"
-~-~~-~~~-~~-~-
____________________________________________
Founded in 2005, Hak5's mission is to advance the InfoSec industry. We do this through our award winning educational podcasts, leading pentest gear, and inclusive community – where all hackers belong.
____________________________________________
This week on HakTip, Shannon pinpoints an exploitation using Wireshark.
Working on the shoulders of last week's episode, this week we'll discuss what exploits look like in Wireshark. The example I'm sharing is from Practical Packet Analysis, a book by Chris Sanders about Wireshark.
Our example packet shows what happens when a user visits a malicious site using a bad version of IE. This is called spear phishing. First, we have HTTP traffic on port 80. We notice there is a 302 moved response from the malicious site and the location is all sorts of weird. Then a bunch of data gets transferred from the new site to the user. Click Follow TCP Stream. If you scroll down, you see some weird gibberish that doesn't make sense and an iframe script. In this case, it's the exploit being sent to the user.
Scroll down to packet 21 and take a look at the .gif GET request. Lastly, Follow packet 25's TCP Stream. This shows us a windows command shell, and the attacker gaining admin priveledges to view our user's files. FREAKY. But now a network admin could use their intrusion detection system to set up a new alarm whenever an attack of this nature is seen.
If someone is trying to do a MITM attack on a user, it might look like our next example packet. 54 and 55 are just ARP packets being sent back and forth, but in packet 56 the attacker sends another ARP packet with a different MAC address for the router, thereby sending the user's data to the attacker then to the router. Compare 57 to 40, and you see the same IP address, but different macs for the destination. This is ARP cache Poisoning.
-~-~~-~~~-~~-~-
Please watch: "Bash Bunny Primer - Hak5 2225"
-~-~~-~~~-~~-~-
____________________________________________
Founded in 2005, Hak5's mission is to advance the InfoSec industry. We do this through our award winning educational podcasts, leading pentest gear, and inclusive community – where all hackers belong.
Комментарии
 0:06:07
0:06:07
 0:05:16
0:05:16
 0:18:59
0:18:59
 0:10:41
0:10:41
 0:07:06
0:07:06
 0:06:16
0:06:16
 0:10:25
0:10:25
 0:40:04
0:40:04
 0:07:41
0:07:41
 0:07:27
0:07:27
 0:15:55
0:15:55
 0:08:17
0:08:17
 0:06:07
0:06:07
 0:07:43
0:07:43
 0:07:09
0:07:09
 0:16:01
0:16:01
 0:08:34
0:08:34
 0:10:00
0:10:00
 0:05:41
0:05:41
 0:07:51
0:07:51
 0:03:22
0:03:22
 0:51:04
0:51:04
 0:02:04
0:02:04
 0:19:08
0:19:08