filmov
tv
Secure Hash Algorithm
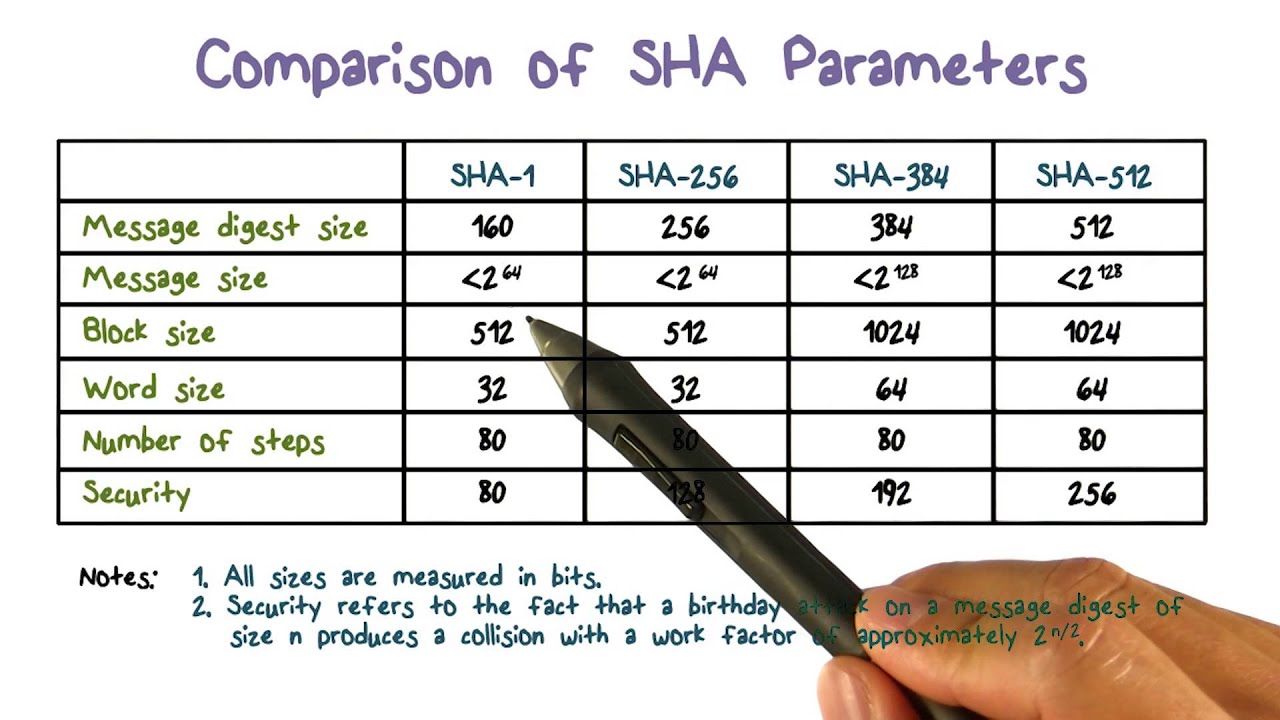
Показать описание
SHA: Secure Hashing Algorithm - Computerphile
Secure Hash Algorithm
#38 SHA ( Secure Hash Algorithm )Algorithm with example |CNS|
SHA-512 ALGORITHM || SECURE HASH ALGORITHM || CRYPTOGRAPHIC HASH FUNCTIONS || NETWORK SECURITY
Hashing, Hashing Algorithms, and Collisions - Cryptography - Practical TLS
SHA 1 | Secure Hash Algorithm | Working of SHA 1 | Parameters of SHA512 and SHA 256
SHA-1 (Secure Hash Algorithm - 1) Part-1 Working Explained in Hindi
SHA-256 | COMPLETE Step-By-Step Explanation (W/ Example)
vpn configuration | SITE TO SITE VPN | isakmp | esp | ipsec vpn LAB
What is a Cryptographic Hashing Function? (Example + Purpose)
How Does SHA-1 Work - Intro to Cryptographic Hash Functions and SHA-1
SHA 256 | SHA 256 Algorithm Explanation | How SHA 256 Algorithm Works | Cryptography | Simplilearn
Passwords & hash functions (Simply Explained)
How secure is 256 bit security?
SHA 512 - Secure Hash Algorithm - Step by Step Explanation - Cryptography - Cyber Security - CSE4003
NETWORK SECURITY - SHA 512 (AUTHENTICATION ALGORITHM)
What Is Hashing? | What Is Hashing With Example | Hashing Explained Simply | Simplilearn
INS: Unit-5 SHA -512 (Secure Hash Algorithm)
SHA-1 (Secure hash Algorithm) working in English | CSS series
Secure Hash Algorithm Explained (SHA)
SHA – Secure Hash Algorithm in Hindi - Properties, Working, Comparison b/w SHA and MD5
How does SHA-256 work? (full explanation)
How hash function work?
Secured Hash Algorithm
Комментарии
 0:10:21
0:10:21
 0:02:14
0:02:14
 0:05:34
0:05:34
 0:26:58
0:26:58
 0:11:42
0:11:42
 0:11:42
0:11:42
 0:10:52
0:10:52
 0:13:01
0:13:01
 1:16:45
1:16:45
 0:07:08
0:07:08
 0:12:16
0:12:16
 0:14:50
0:14:50
 0:07:28
0:07:28
 0:05:06
0:05:06
 0:53:13
0:53:13
 0:42:16
0:42:16
 0:09:45
0:09:45
 0:14:58
0:14:58
 0:22:42
0:22:42
 0:09:20
0:09:20
 0:10:16
0:10:16
 0:19:24
0:19:24
 0:04:29
0:04:29
 0:05:58
0:05:58