filmov
tv
pico2024 format string 1

Показать описание
The format string vulnerability allows us to walk up the stack and view its contents. Since this is a 64-bit executable, we need to use %llx to view the 64-bit numbers in hexadecimal. Using %16$llx allows us to walk 16 spaces up the stack. We then need to reverse the endianness to get the flag string (since the Intel architecture is little endian, and converting hex to ascii).
pico2024 format string 1
format string 1 | Binary Exploitation | picoCTF 2024
picoCTF 2024 Challenge Series - Beginner's Cybersecurity - Format String 0
FORMAT STRINGS (PicoCTF 2024 #7: Format String 0)
[WRITEUP] picoCTF (2024) - format-string-1
Format String printf Vulnerabilities (PicoCTF 2022 #46 'flag-leak')
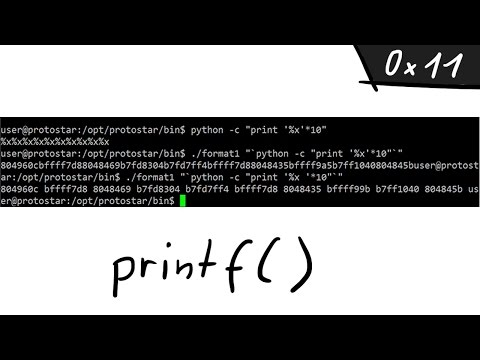
A simple Format String exploit example - bin 0x11
pico2024 format string 3
pico2024 CanYouSee
pico2024 binhexa
pico2024 binary search
Format String Exploit Troubleshooting Over Twitter - bin 0x11 b
Understanding Format String Vulnerability || Binary Exploitation - 0x11
pico2024 heap 2
pico2024 heap 3
#5 - Lỗi format string - stringzz (picoCTF 2019)
Комментарии
 0:14:26
0:14:26
 0:02:35
0:02:35
 0:12:52
0:12:52
 0:01:45
0:01:45
![[WRITEUP] picoCTF (2024)](https://i.ytimg.com/vi/Q6ChEX5ig04/hqdefault.jpg) 0:11:19
0:11:19
 0:19:44
0:19:44
 0:10:01
0:10:01
 0:09:47
0:09:47
 0:03:03
0:03:03
 0:03:25
0:03:25
 0:02:11
0:02:11
 0:24:59
0:24:59
 0:15:50
0:15:50
 0:05:38
0:05:38
 0:04:55
0:04:55
 0:26:23
0:26:23