filmov
tv
How to integrate Okta with AWS API Gateway JWT Authorizer?

Показать описание
This video explains how to generate a JWT Access Token using Okta and use that token to Authorize API endpoints hosted in AWS API Gateway.
#aws #amazonwebservices #openid #okta #authentication #iam #identity #apigateway #api #security
#aws #amazonwebservices #openid #okta #authentication #iam #identity #apigateway #api #security
Adding Okta Authentication to a Web Application
Creating an OIDC Web App | Okta Support
How to Integrate Okta with Duo Universal Prompt | Okta Support
How to Integrate Okta with Jamf Account
Okta integration with Active directory
Integration of GitHub with Okta
How to integrate Okta with AWS API Gateway JWT Authorizer?
How to Add Applications to Okta
Okta Integration
Okta Integration in ServiceNow for SSO
Configuring Routing Rules for New Users in Okta with AzureAD Integration | Okta Support
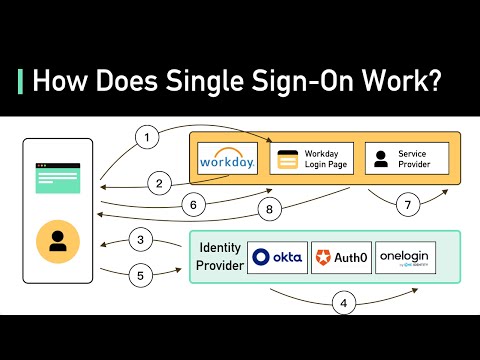
What Is Single Sign-on (SSO)? How It Works
Okta and SalesForce SAML SSO Integration
SailPoint - Okta Integration Demonstration Video
Integrating Okta with AWS SSO in AWS Control Tower | Amazon Web Services
IT: Okta SSO SAML Integration (Setting up Office 365 SSO)
How to integrate Okta with Cisco Umbrella #saml #api
Getting Started with Semaphore - How to Integrate Okta
Azure AD as IDP in Okta - Log in to Okta with Azure AD
Sync/Push Users from Okta to Active Directory | Okta Support
OKTA integration with office 365
Okta integration with LDAP
Creating a Custom SAML App | Okta Support
VMware Identity Services: Okta Integration - Feature Walk-through
Комментарии
 0:08:39
0:08:39
 0:04:41
0:04:41
 0:02:53
0:02:53
 0:04:09
0:04:09
 0:05:18
0:05:18
 0:02:54
0:02:54
 0:19:32
0:19:32
 0:09:13
0:09:13
 0:02:09
0:02:09
 0:03:41
0:03:41
 0:02:02
0:02:02
 0:04:54
0:04:54
 0:10:54
0:10:54
 0:02:14
0:02:14
 0:06:51
0:06:51
 0:08:51
0:08:51
 0:11:50
0:11:50
 0:09:38
0:09:38
 0:00:52
0:00:52
 0:05:54
0:05:54
 0:03:52
0:03:52
 0:14:15
0:14:15
 0:02:41
0:02:41
 0:07:16
0:07:16