filmov
tv
HTML Ping Attribute Explained ˂ href = ‘http://youtube.com’ ping = ‘http://localhost:8080’ ˃

Показать описание
I͕n this video I explain how PING attribute in an anchor HTML element works.
0:00 Intro
1:00 Ping Explained
7:00 Ping Use in Google Search (Chrome)
9:00 Ping is Disabled FireFox
11:00 The Danger of POST
͔͔͔͔͔͔🏭 Backend Engineering Videos
💾 Database Engineering Videos
🛰 Network Engineering Videos
🏰 Load Balancing and Proxies Videos
🐘 Postgres Videos
🚢Docker
🧮 Programming Pattern Videos
🛡 Web Security Videos
🦠 HTTP Videos
🐍 Python Videos
🔆 Javascript Videos
Become a Member
Support me on PayPal
Become a Patreon
Stay Awesome,
Hussein
0:00 Intro
1:00 Ping Explained
7:00 Ping Use in Google Search (Chrome)
9:00 Ping is Disabled FireFox
11:00 The Danger of POST
͔͔͔͔͔͔🏭 Backend Engineering Videos
💾 Database Engineering Videos
🛰 Network Engineering Videos
🏰 Load Balancing and Proxies Videos
🐘 Postgres Videos
🚢Docker
🧮 Programming Pattern Videos
🛡 Web Security Videos
🦠 HTTP Videos
🐍 Python Videos
🔆 Javascript Videos
Become a Member
Support me on PayPal
Become a Patreon
Stay Awesome,
Hussein
HTML Ping Attribute Explained ˂ href = ‘http://youtube.com’ ping = ‘http://localhost:8080’ ˃...
What is the Ping attribute of HTML Anchor Tag? | HTML Anchor Tag | 10 usages of Anchor Tag | Course
Testing anchor element with ping attribute
How to test ping attribute in Cypress?
#Powershell #HTML based ping monitor Dashboard Demo
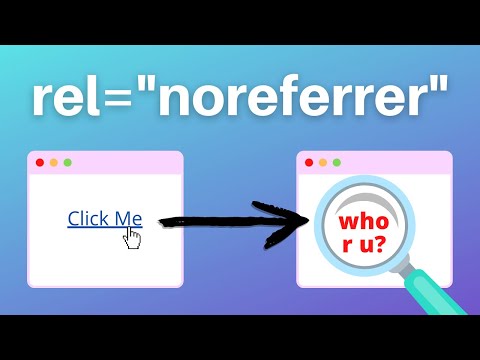
When To Use noreferrer In Your Links (with referrer policy examples)
Coding for 1 Month Versus 1 Year #shorts #coding
Ping 2021: Aula 0x21 - HTML e CSS
Best Programming Languages #programming #coding #javascript
Ping 2021: Aula 0x20 - URLs
You're (Probably) Using Prettier Wrong
CSS Animation Ping Pong Game Design || Ping Pong Animation Game Design Using HTML And CSS
Refresher Crash Course for Desktop Support, Network Admin, System Admin, Web Dev, Help Desk
Anchor tag (a tag) part 4 - html 5 tutorial in hindi - urdu with name attribute - Class - 07
Do you want to better your life? #philippines #angelescity #expat #pampanga #travelvlog
22 - ping-monitor - icons
HTML, CSS, & JavaScript | ping coming soon page master
'Basic Authentication' in Five Minutes
HTML5 video accessibility and the WebVTT file format
Favicons the Right Way
Create Ping Pong Game Using JavaScript and HTML5 | JavaScript Project For Beginners
Blue Prism Video Tutorial | 022 | Automating web applications - Part 1 - Spying HTML elements
Ping single column coming soon Page | Frontend Mentor Challenge | #frontendmentor
Ping Pong Game using (HTML, CSS AND JAVASCRIPT)
Комментарии
 0:14:37
0:14:37
 0:04:21
0:04:21
 0:04:56
0:04:56
 0:11:34
0:11:34
 0:00:55
0:00:55
 0:07:36
0:07:36
 0:00:24
0:00:24
 0:07:52
0:07:52
 0:00:16
0:00:16
 0:06:56
0:06:56
 0:06:04
0:06:04
 0:11:14
0:11:14
 0:56:31
0:56:31
 0:06:27
0:06:27
 0:00:16
0:00:16
 0:06:54
0:06:54
 0:22:35
0:22:35
 0:05:07
0:05:07
 0:27:22
0:27:22
 0:18:07
0:18:07
 0:55:45
0:55:45
 0:10:18
0:10:18
 0:48:38
0:48:38
 0:03:37
0:03:37