filmov
tv
Tracking Cyber Intruders with Jupyter and Python - Python Bytes Live Stream Episode 276

Показать описание
Tracking Cyber Intruders with Jupyter and Python - Python Bytes Live Stream Episode 276
▬▬▬▬▬▬ Chapters ▬▬▬▬▬▬▬
00:00 - Introduction
10:10 - DevDocs
15:46 - MSTICPy
27:40 - FusionAuth (Sponsor)
28:51 - The Right Way To Compare Floats in Python
35:05 - Pypyr
39:47 - Pygments
45:13 - Extras
49:04 - Joke
▬▬▬▬▬▬ Full show notes ▬▬▬▬▬▬▬
▬▬▬▬▬▬ More Episodes ▬▬▬▬▬▬▬
▬▬▬▬▬▬ Dive Deeper ▬▬▬▬▬▬▬
▬▬▬▬▬▬ Chapters ▬▬▬▬▬▬▬
00:00 - Introduction
10:10 - DevDocs
15:46 - MSTICPy
27:40 - FusionAuth (Sponsor)
28:51 - The Right Way To Compare Floats in Python
35:05 - Pypyr
39:47 - Pygments
45:13 - Extras
49:04 - Joke
▬▬▬▬▬▬ Full show notes ▬▬▬▬▬▬▬
▬▬▬▬▬▬ More Episodes ▬▬▬▬▬▬▬
▬▬▬▬▬▬ Dive Deeper ▬▬▬▬▬▬▬
Tracking Cyber Intruders with Jupyter and Python - Python Bytes Live Stream Episode 276
Intruder Detection System
Threat Hunting Course Free- Day 9, Hunt on Cloud, AWS
AE024 | Intruder Detection System Using Face Recognition
BZAR – Hunting Adversary Behaviors with Zeek and ATT&CK - SANS THIR Summit 2019
Cyber Threat Hunting | Chris Brenton | October 2020 | 4 Hours
Threat Hunting Tutorial: How to use Network Metadata to detect threats
Hazard Identification and Detection using Machine Learning Approach using Python - 1Crore Projects
Gabrielle Hempel - Let's Get Cloud: Threat Hunting in Cloud-Based Environments
Stay ahead of the game: automate your threat hunting workflows
Cyber Threat Workshop - 2-3-2022 - Red Teaming: How to identify Attack Surface Risks
Tracking and Behavior Augmented Activity Recognition for Multiple Inhabitants
Blue-Team-as-Code: Lessons From Real-world Red Team Detection Automation Using Logs
MovieSent Dual Approach Sentiment Analysis #Easy project python 2025
Threat Hunting Training | April 2023
Threat Hunting Masterclass: Three Data Science Notebooks to Find Bad Actors in Your Network Logs
Ninjas On Rooftops - Making Linux Threat Hunting More Effective
07. x33fcon 2018 - What The HELK? Enabling Graph Analytics for Threat Hunting by Cyb3rWard0g
Detecting Security Issues Using Exploratory Data Analysis - O'Reilly Webcast
Face Recognition Python Project | Face Detection Using OpenCV Python - Complete Tutorial
Attack with Sniffing on Victim Bring images in when browsing
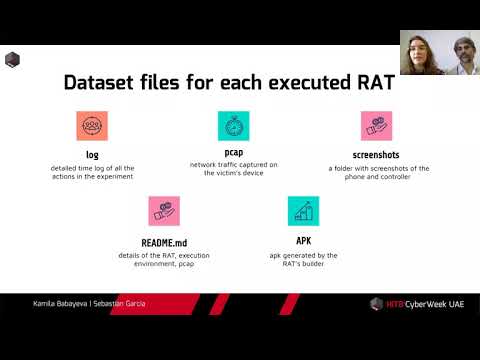
#HITBCyberWeek D1T2 - Android RATs Detection With A Machine Learning-based Python IDS
Webinar: Threat Hunting Lessons You Won’t Learn From Guides and Whitepapers
OSINT Curious Live Stream - Location of an IP Address
Комментарии
 0:49:59
0:49:59
 0:04:46
0:04:46
 0:18:07
0:18:07
 0:03:59
0:03:59
 0:31:16
0:31:16
 3:54:49
3:54:49
 0:58:01
0:58:01
 0:05:01
0:05:01
 0:20:12
0:20:12
 0:30:26
0:30:26
 2:01:55
2:01:55
 0:11:04
0:11:04
 0:37:15
0:37:15
 0:00:44
0:00:44
 5:01:20
5:01:20
 0:59:15
0:59:15
 0:03:47
0:03:47
 0:48:00
0:48:00
 0:54:18
0:54:18
 0:19:19
0:19:19
 0:04:08
0:04:08
 0:55:29
0:55:29
 1:11:59
1:11:59
 0:38:03
0:38:03