filmov
tv
🎥 Identifying Flows to and from Specific Processes with eBPF Probes 🎥
Показать описание
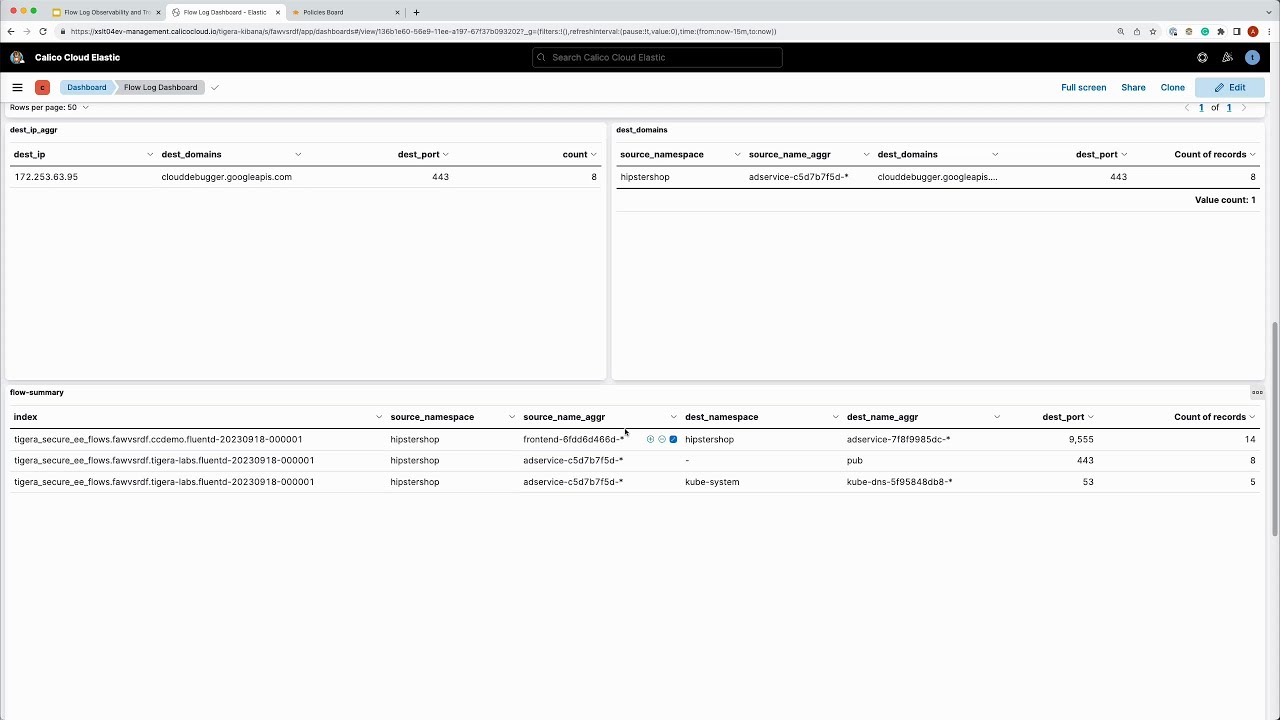
Welcome everyone to this next example. In this video, we will look at how to identify flows to and from specific processes using eBPF probes.
📺 Video: Identifying Flows to and from Specific Processes with eBPF Probes
🔑 Key Highlights:
Introduction to process-level flow visibility using eBPF probes.
How flow logs are enriched with metadata including process ID, process name, and arguments.
Practical use cases for identifying and analyzing specific process flows.
Detailed examples of querying and filtering flow logs based on process information.
Insights into forensic analysis and investigating potential security incidents.
📜 Chapters:
0:00 Introduction to Process-Level Flow Visibility
1:00 Understanding Flow Logs Enriched with Process Metadata
1:47 Practical Use Case: Identifying Log4j Vulnerability Flows by Filtering Flow Logs by process Information
6:34 Summary
🎓 What You'll Learn:
How to utilize eBPF probes for detailed process-level visibility in flow logs.
Techniques for querying and filtering flow logs based on specific processes and arguments.
Practical insights into identifying and analyzing network traffic related to specific processes.
How to leverage process-level flow data for forensic analysis and security investigations.
Enhance your observability and troubleshooting skills with this comprehensive video on identifying flows to and from specific processes using eBPF probes.
📌 If you found this video helpful, please like, comment, and subscribe for more content on Kubernetes security and observability. Check out our other videos in this series to learn more about flow log observability and troubleshooting.
#Microsegmentation #Kubernetes #ContainerSecurity #Calico #NetworkSecurity #PolicyManagement #Observability #Troubleshooting #eBPFProbes #FlowLogs
📺 Video: Identifying Flows to and from Specific Processes with eBPF Probes
🔑 Key Highlights:
Introduction to process-level flow visibility using eBPF probes.
How flow logs are enriched with metadata including process ID, process name, and arguments.
Practical use cases for identifying and analyzing specific process flows.
Detailed examples of querying and filtering flow logs based on process information.
Insights into forensic analysis and investigating potential security incidents.
📜 Chapters:
0:00 Introduction to Process-Level Flow Visibility
1:00 Understanding Flow Logs Enriched with Process Metadata
1:47 Practical Use Case: Identifying Log4j Vulnerability Flows by Filtering Flow Logs by process Information
6:34 Summary
🎓 What You'll Learn:
How to utilize eBPF probes for detailed process-level visibility in flow logs.
Techniques for querying and filtering flow logs based on specific processes and arguments.
Practical insights into identifying and analyzing network traffic related to specific processes.
How to leverage process-level flow data for forensic analysis and security investigations.
Enhance your observability and troubleshooting skills with this comprehensive video on identifying flows to and from specific processes using eBPF probes.
📌 If you found this video helpful, please like, comment, and subscribe for more content on Kubernetes security and observability. Check out our other videos in this series to learn more about flow log observability and troubleshooting.
#Microsegmentation #Kubernetes #ContainerSecurity #Calico #NetworkSecurity #PolicyManagement #Observability #Troubleshooting #eBPFProbes #FlowLogs
 0:05:03
0:05:03
 0:07:12
0:07:12
 0:04:59
0:04:59
 0:02:24
0:02:24
 0:16:05
0:16:05
 0:00:34
0:00:34
 0:02:16
0:02:16
 0:00:17
0:00:17
 0:00:36
0:00:36
 0:58:10
0:58:10
 0:19:11
0:19:11
 0:16:20
0:16:20
 0:13:25
0:13:25
 0:03:44
0:03:44
 0:21:16
0:21:16
 0:00:51
0:00:51
 0:00:13
0:00:13
 0:02:56
0:02:56
 0:38:17
0:38:17
 0:01:12
0:01:12
 0:00:12
0:00:12
 0:00:12
0:00:12
 0:00:16
0:00:16
 0:34:10
0:34:10