filmov
tv
Understanding Kerberoasting

Показать описание
Kerberoasting is the attack that keeps on giving for adversaries and penesters alike. First documented in 2014 by Tim Medin, Kerberoasting is a tactic that can be used after an initial compromise to gain access to alternate accounts in an Active Directory domain.
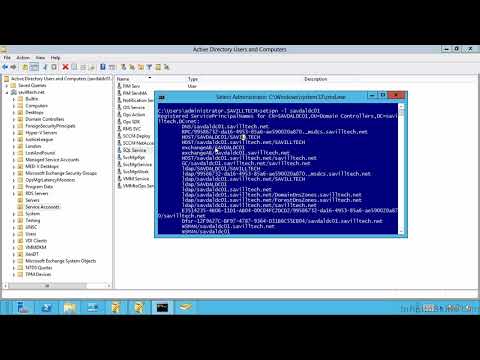
It typically involves an attacker issuing a series of LDAP queries to a Domain Controller in search of user accounts that possess a value known as a Service Principal Name (SPN).
If this value is set on an account, an attacker can request a service ticket (ST) for the identity, which is encrypted with the account’s NT hash. This service ticket can then be cracked offline by the attacker, which, if successful, will allow them to retrieve the cleartext password of the account.
It typically involves an attacker issuing a series of LDAP queries to a Domain Controller in search of user accounts that possess a value known as a Service Principal Name (SPN).
If this value is set on an account, an attacker can request a service ticket (ST) for the identity, which is encrypted with the account’s NT hash. This service ticket can then be cracked offline by the attacker, which, if successful, will allow them to retrieve the cleartext password of the account.
Learn Active Directory Kerberoasting
Understanding Kerberoasting
Attacking active directory | kerberoasting
Kerberoasting Explained
Kerberoasting Explained | Kerberos Authentication | Active Directory
How Kerberos Works
Attacking Active Directory - Kerberoasting
Kerberoasting Attack Demo
Advent of Cyber 2024 - Day 15: Active Directory | TryHackMe | CyberPranava
Kerberos Simplified - CISSP Exam Prep
AS-REP Roasting & Kerberoasting | Simple Explained
Attack Tutorial: How the Kerberoasting Attack Works
⚠️ Don't Get Roasted! Understanding Kerberoasting Attacks on Your System
Top Active Directory Attacks: Understand, then Prevent and Detect
OSCP Guide to Kerberoasting - Active Directory
Kerberoasting
Hacking Active Directory for Beginners (over 5 hours of content!)
Advanced: Kerberoasting Fundamentals
Kerberoasting - what can we really do
Emulating and Detecting Kerberoasting | Red Canary
SIEGECAST: Kerberoasting & Attacks 101
Active Directory Kerberoasting Attack: A Technical Deep Dive #activedirectory #kerberoasting
0709 Understanding Service Principal Names SPNS
SpecterOps Webinar Week Kerberoasting Revisted
Комментарии
 0:22:05
0:22:05
 0:14:23
0:14:23
 0:06:17
0:06:17
 0:04:41
0:04:41
 0:11:15
0:11:15
 0:02:19
0:02:19
 0:13:22
0:13:22
 0:06:43
0:06:43
 0:54:30
0:54:30
 0:04:16
0:04:16
 0:10:17
0:10:17
 0:04:25
0:04:25
 0:03:12
0:03:12
 0:40:01
0:40:01
 0:18:07
0:18:07
 0:38:58
0:38:58
 5:16:30
5:16:30
 1:52:37
1:52:37
 0:17:15
0:17:15
 0:38:21
0:38:21
 1:10:52
1:10:52
 0:08:23
0:08:23
 0:03:20
0:03:20
 0:42:07
0:42:07