filmov
tv
Step-by-step Windows Hello PIN for Hybrid Windows 10 using Key-based authentication and Intune

Показать описание
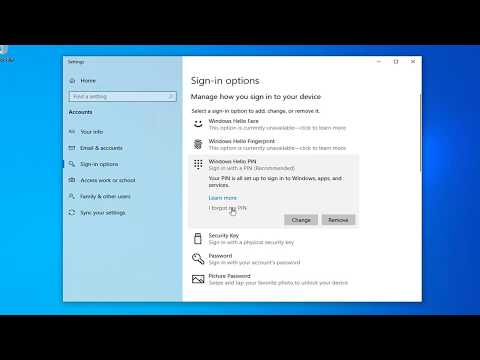
In this video we see a demo of implementing Windows Hello PIN based authentication for hybrid joined, SCCM Intune co managed devices by setting Intune device configuration.
Here are the custom CSP settings
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/UsePassportForWork = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/Digits = 1 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/History = 5 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/Expiration = 90 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/RequireSecurityDevice = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/EnablePinRecovery = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/UseCertificateForOnPremAuth = false (Boolean)
./Device/Vendor/MSFT/PassportForWork/Biometrics/UseBiometrics = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/Biometrics/FacialFeaturesUseEnhancedAntiSpoofing = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/MinimumPINLength = 6 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/MaximumPINLength = 16 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/SpecialCharacters = 1 (Integer)
Here are the custom CSP settings
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/UsePassportForWork = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/Digits = 1 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/History = 5 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/Expiration = 90 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/RequireSecurityDevice = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/EnablePinRecovery = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/UseCertificateForOnPremAuth = false (Boolean)
./Device/Vendor/MSFT/PassportForWork/Biometrics/UseBiometrics = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/Biometrics/FacialFeaturesUseEnhancedAntiSpoofing = true (Boolean)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/MinimumPINLength = 6 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/MaximumPINLength = 16 (Integer)
./Device/Vendor/MSFT/PassportForWork/AAD Tenant ID/Policies/PINComplexity/SpecialCharacters = 1 (Integer)
Комментарии
 0:01:47
0:01:47
 0:13:46
0:13:46
 0:03:44
0:03:44
 0:04:09
0:04:09
 0:01:01
0:01:01
 0:03:03
0:03:03
 0:01:43
0:01:43
 0:01:57
0:01:57
 0:50:17
0:50:17
 0:02:06
0:02:06
 0:16:10
0:16:10
 0:08:49
0:08:49
 0:02:05
0:02:05
 0:04:33
0:04:33
 0:03:32
0:03:32
 0:03:22
0:03:22
 0:22:45
0:22:45
 0:00:17
0:00:17
 0:00:42
0:00:42
 0:05:51
0:05:51
 0:03:06
0:03:06
 1:00:49
1:00:49
 0:12:15
0:12:15
 0:02:26
0:02:26