filmov
tv
SAP CYBER SECURITY SAP* Parameter

Показать описание
Surviving an SAP Audit: A Practical Guide to SAP Audit
Security, Audit and Control Features SAP ERP, 4th EditioN
SAP License Management Step by Step Guide
Auditing and GRC Automation in SAP
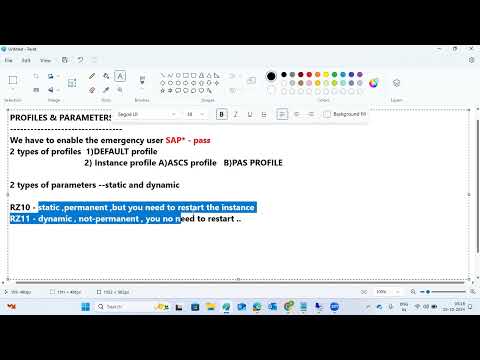
In SAP there is parameter login/no_automatic_user_sapstar whose default value is 1. If the value is set to 1, automatic login of sap* into SAP System using password PASS won’t be allowed.
When the parameter login/no_automatic_user_sapstar to 0 in both the default profile and the instance profile and restart the instance. So, of sap* with default password will be enabled.
When login/no_automatic_user_sapstar is set to 0, the worst thing you can do from a security point of view is to delete the SAP* user, because it enables the hardcoded SAP* user in the SAP kernel. The hardcoded SAP* user will always have password 'pass' and since this is well known, it is a big security breach.
The way to disable SAP* user, is to assign a secure password, lock the user and set a validity date in the past. The SAP* user should always be locked, except when the system administrator needs it from time to time.
[ Free Webinar] See how Automating Detecting and implementing SAP Notes can help you improve your operations, and secure your SAP Landscape
#ExpressGRC #SAPGRC #SAPSECURITY #GRC #SAPCYBERSECURITY
Click Here to Register
Security, Audit and Control Features SAP ERP, 4th EditioN
SAP License Management Step by Step Guide
Auditing and GRC Automation in SAP
In SAP there is parameter login/no_automatic_user_sapstar whose default value is 1. If the value is set to 1, automatic login of sap* into SAP System using password PASS won’t be allowed.
When the parameter login/no_automatic_user_sapstar to 0 in both the default profile and the instance profile and restart the instance. So, of sap* with default password will be enabled.
When login/no_automatic_user_sapstar is set to 0, the worst thing you can do from a security point of view is to delete the SAP* user, because it enables the hardcoded SAP* user in the SAP kernel. The hardcoded SAP* user will always have password 'pass' and since this is well known, it is a big security breach.
The way to disable SAP* user, is to assign a secure password, lock the user and set a validity date in the past. The SAP* user should always be locked, except when the system administrator needs it from time to time.
[ Free Webinar] See how Automating Detecting and implementing SAP Notes can help you improve your operations, and secure your SAP Landscape
#ExpressGRC #SAPGRC #SAPSECURITY #GRC #SAPCYBERSECURITY
Click Here to Register
 0:01:31
0:01:31
 0:02:20
0:02:20
 0:11:36
0:11:36
 0:11:39
0:11:39
 0:02:48
0:02:48
 0:04:34
0:04:34
 0:02:15
0:02:15
 0:06:08
0:06:08
 0:34:38
0:34:38
 0:34:46
0:34:46
 0:01:05
0:01:05
 0:02:07
0:02:07
 0:06:58
0:06:58
 0:01:40
0:01:40
 0:46:47
0:46:47
 0:03:04
0:03:04
 0:02:28
0:02:28
 0:02:15
0:02:15
 0:06:00
0:06:00
 0:08:03
0:08:03
 0:07:46
0:07:46
 0:34:16
0:34:16
 0:05:39
0:05:39
 0:01:59
0:01:59