filmov
tv
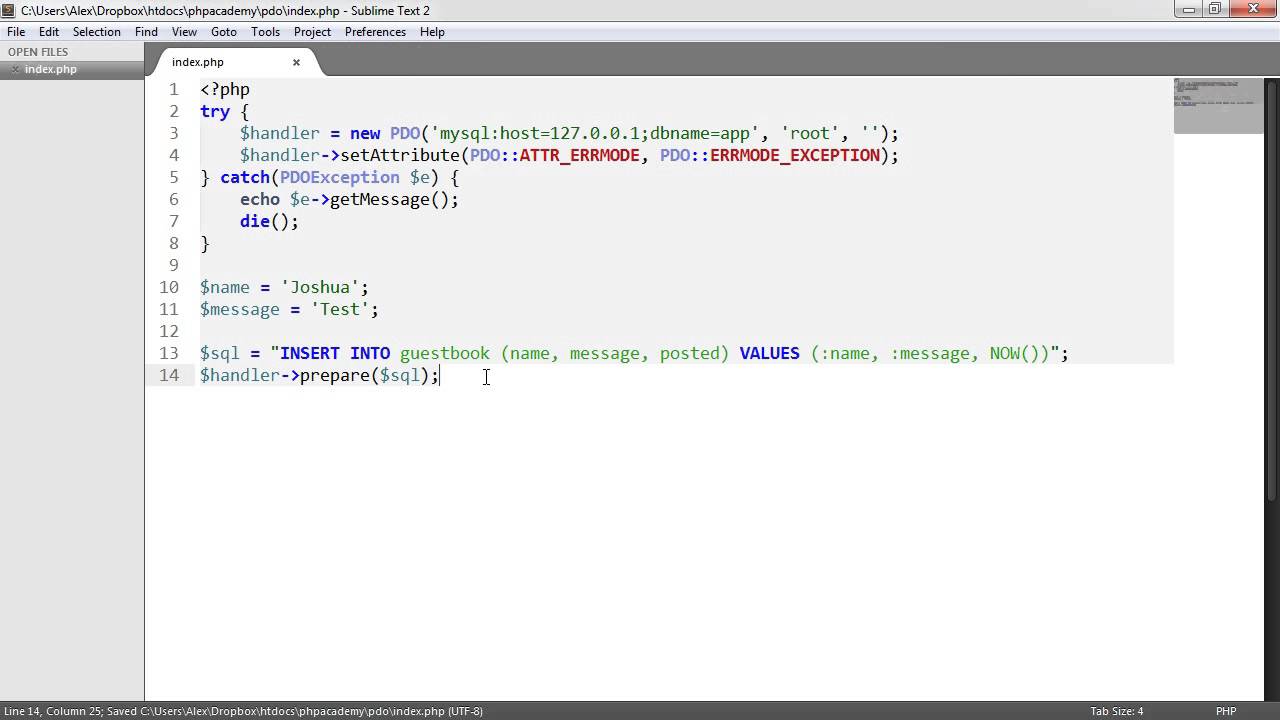
PHP Data Objects (PDO): Prepared statements (Part 6/8)
Показать описание
Official site
PHP Data Objects (PDO): Prepared statements (Part 6/8)
17: Query A Database Using OOP PHP | Prepared Statements Using PDO | Object Oriented PHP Tutorial
PHP PDO Tutorial Part 1 - Prepared Statements - SQL Injection - Full PHP 8 Tutorial
Fetch Data from Mysql in PHP using PDO - PHP Data Object
MYSQL connection using PHP Data Objects(PDO) - Quick programming tutorial
PDO Crash Course (PHP)
Query A Database Using PDO In OOP PHP | Object Oriented PHP Tutorial | PHP Tutorial | mmtuts
PHP - PDO Prepared Statements
Database Systems - Web Database Programming with PHP Data Objects PDO - APPFICIAL
PHP PDO prepare vs PDO no prepare
PHP PDO Prepared Statements Tutorial
PHP Tutorial - #95 - How to Select Data Using Prepared Statements (PDO) - fetch and fetchAll
Insert data into Mysql in PHP using PDO - PHP Data Object
Avoid SQL injection attacks in PHP using PDO
CTEC 127: Getting Started with PDO in PHP
PHP Data Objects (PDO): Connecting (Part 1/8)
CRUD Operations with PHP, PDO and Prepared Statements || Fully Secured || Easy Coding
PHP Data Object (PDO): Fetch Data From Table using Prepare Statement Unnamed Parameter
Connect MySQL Database in PHP via PDO - PHP Data Object
PHP Tutorial - #92 - How to Insert Data Using Prepared Statements (PDO)
PDO (PHP Data Object) - Delete Mysql Table data in PHP
40: What are Prepared Statements and how to use them | PHP tutorial | Learn PHP programming
Introduction to PDO and Prepared Statements for MySQL Queries
PHP with MySQL: PDO and Prepared Statements
Комментарии
 0:07:09
0:07:09
 0:19:59
0:19:59
 0:25:36
0:25:36
 0:09:01
0:09:01
 0:23:36
0:23:36
 0:45:35
0:45:35
 0:13:27
0:13:27
 0:09:49
0:09:49
 0:05:14
0:05:14
 0:02:21
0:02:21
 0:02:54
0:02:54
 0:02:23
0:02:23
 0:12:42
0:12:42
 0:04:02
0:04:02
 0:33:21
0:33:21
 0:11:31
0:11:31
 0:09:54
0:09:54
 0:10:42
0:10:42
 0:08:57
0:08:57
 0:03:17
0:03:17
 0:07:01
0:07:01
 0:18:12
0:18:12
 0:21:22
0:21:22
 0:00:50
0:00:50