filmov
tv
Massive DDoS attack explained

Показать описание
The Spamhaus project, an international non-profit organization that tracks spam, reported that it has been the target of a persistent distributed denial of service attack. Spamhaus provides spam filtering data to the internet.
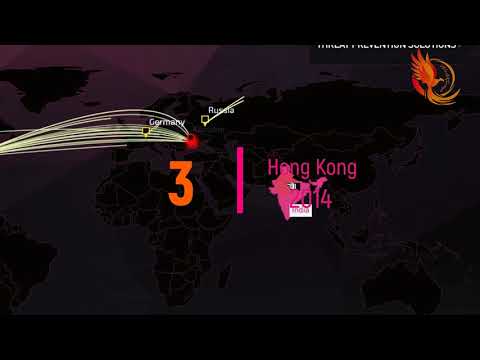
The attackers disguised themselves as Spamhaus to send requests to Open DNS servers. The Open DNS servers replied by sending massive waves of information to Spamhaus' servers.
Spamhaus got help from CloudFlare, which used a technique called 'anycast' to send the flood of data to mirrored servers in other locations to relieve the stress on Spamhaus.
But the flood of data was so great that CloudFlare's servers began to overload the Tier 2 internet service providers on which they relied. The Tier 2 servers blocked the traffic from Spamhaus, causing the traffic to bypass them and head directly to Tier 1 internet service providers in Europe, which connect to each other at the London Internet Exchange.
Internet exchanges such as the one in London connect Tier 1 internet service providers. Tier 1 internet service providers connect Tier 2 networks.
But the attack was so massive that on March 23, the London Internet Exchange suffered an outage for one hour. The perpetrator of the attack on Spamhaus has not yet been identified.
 0:01:15
0:01:15
 0:03:31
0:03:31
 0:09:52
0:09:52
 0:00:34
0:00:34
 0:06:32
0:06:32
 0:36:18
0:36:18
 0:01:38
0:01:38
 0:04:28
0:04:28
 0:02:21
0:02:21
 0:03:51
0:03:51
 0:16:41
0:16:41
 0:03:15
0:03:15
 0:08:35
0:08:35
 0:08:17
0:08:17
 0:04:31
0:04:31
 0:00:07
0:00:07
 0:04:54
0:04:54
 0:00:53
0:00:53
 0:00:16
0:00:16
 0:05:26
0:05:26
 0:06:23
0:06:23
 0:25:51
0:25:51
 0:21:57
0:21:57
 0:00:29
0:00:29