filmov
tv
NordVPN Hacked? What Really Happened

Показать описание
Information has recently surfaced about a NordVPN breach caused by vulnerabilities in a third-party datacenter’s server. We’d like to give you a clear timeline of the events followed by some key facts about the NordVPN breach story.
***
***
Key facts
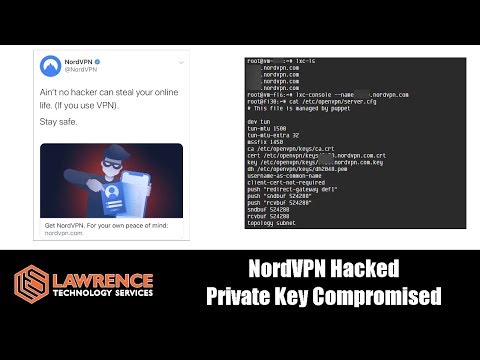
One server was affected in March 2018 in Finland. The rest of our service was not affected. No other servers of any type were put at risk. This was an attack on our server, not our entire service.
The breach was made possible by poor configuration on a third-party datacenter’s part that we were never notified of. Evidence suggests that when the datacenter became aware of the intrusion, they deleted the accounts that had caused the vulnerabilities rather than notify us of their mistake. As soon as we learned of the breach, the server and our contract with the provider were terminated and we began an extensive audit of our service.
No user credentials were affected.
There are no signs that the intruder attempted to monitor user traffic in any way. Even if they had, they would not have had access to those users’ credentials.
The attacker did acquire TLS keys that, under extraordinary circumstances, could be used to attack a single user on the web using a specifically targeted and highly sophisticated MITM attack that we detail further below. These keys could not and cannot be used to decrypt any encrypted NordVPN traffic in any form.
Two other VPN providers were impacted in attacks published by the same intruder. We do not believe that this was a targeted attack against NordVPN.
The incident effectively showed that the affected server did not contain any user activity logs. To prevent any similar incidents, among other means, we encrypt the hard disk of each new server we build. The security of our customers is the highest priority to us and we will continue to raise our standards further and further.
Our goal here is to notify and educate the public about this breach. That’s the only way we’ll be able to recover from this significant setback and make our security even tighter.
***
***
Key facts
One server was affected in March 2018 in Finland. The rest of our service was not affected. No other servers of any type were put at risk. This was an attack on our server, not our entire service.
The breach was made possible by poor configuration on a third-party datacenter’s part that we were never notified of. Evidence suggests that when the datacenter became aware of the intrusion, they deleted the accounts that had caused the vulnerabilities rather than notify us of their mistake. As soon as we learned of the breach, the server and our contract with the provider were terminated and we began an extensive audit of our service.
No user credentials were affected.
There are no signs that the intruder attempted to monitor user traffic in any way. Even if they had, they would not have had access to those users’ credentials.
The attacker did acquire TLS keys that, under extraordinary circumstances, could be used to attack a single user on the web using a specifically targeted and highly sophisticated MITM attack that we detail further below. These keys could not and cannot be used to decrypt any encrypted NordVPN traffic in any form.
Two other VPN providers were impacted in attacks published by the same intruder. We do not believe that this was a targeted attack against NordVPN.
The incident effectively showed that the affected server did not contain any user activity logs. To prevent any similar incidents, among other means, we encrypt the hard disk of each new server we build. The security of our customers is the highest priority to us and we will continue to raise our standards further and further.
Our goal here is to notify and educate the public about this breach. That’s the only way we’ll be able to recover from this significant setback and make our security even tighter.
Комментарии
 0:01:46
0:01:46
 0:12:25
0:12:25
 0:03:43
0:03:43
 0:03:29
0:03:29
 0:10:06
0:10:06
 0:11:25
0:11:25
 0:03:30
0:03:30
 0:00:12
0:00:12
 0:07:29
0:07:29
 0:10:17
0:10:17
 0:03:49
0:03:49
 0:06:12
0:06:12
 0:00:46
0:00:46
 0:30:43
0:30:43
 0:00:30
0:00:30
 0:04:23
0:04:23
 0:14:04
0:14:04
 0:00:41
0:00:41
 0:02:49
0:02:49
 0:05:51
0:05:51
 0:07:10
0:07:10
 0:01:12
0:01:12
 0:04:39
0:04:39
 0:07:41
0:07:41