filmov
tv
RuhrSec 2017: 'Rowhammer Attacks: A Walkthrough Guide', Dr. Clémentine Maurice & Daniel Gruss
Показать описание
RuhrSec is the annual English speaking non-profit IT security conference with cutting-edge security talks by renowned experts. RuhrSec is organized by Hackmanit.
🔽 More information ...
Abstract. In the past 2 years the so-called Rowhammer bug has caught the attention of many academic and non-academic researchers. The scary aspect of the Rowhammer bug is that is entirely invalidates software security assumptions. Isolation mechanisms are ineffective to a degree where an attacker can run in a website and compromise the entire host system.
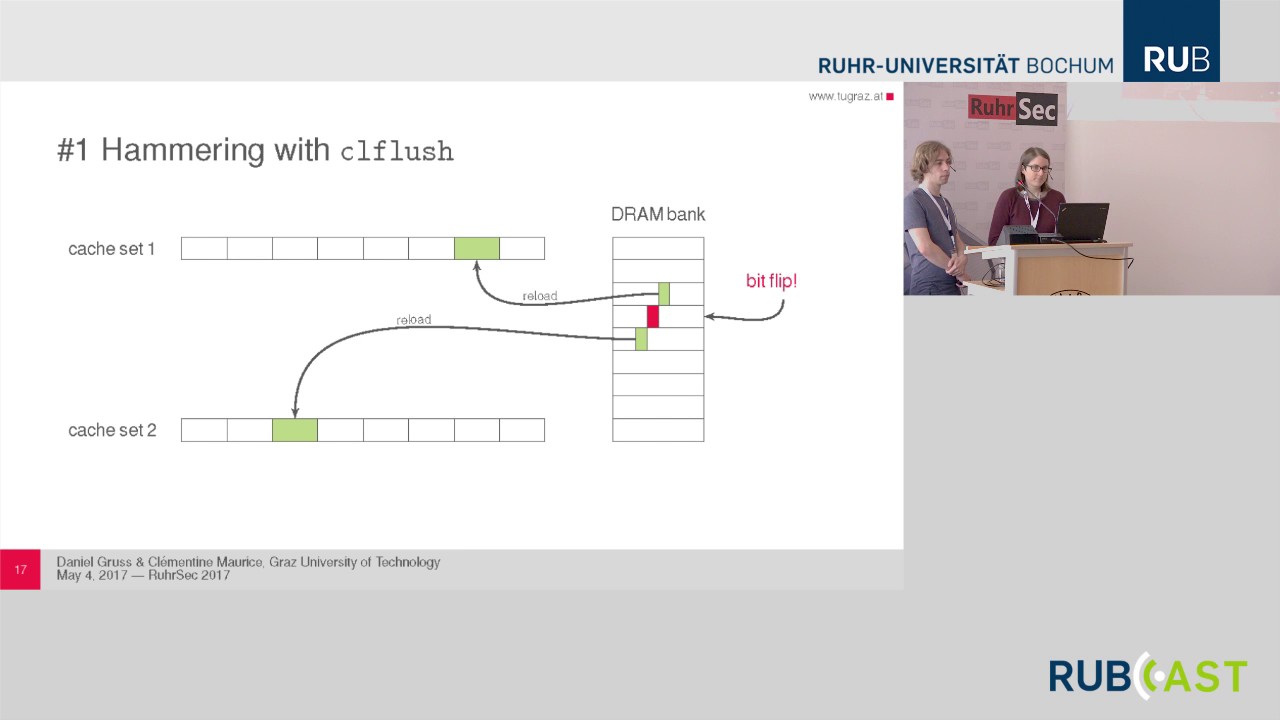
In this walkthrough guide I will walk you through all Rowhammer attacks that have been presented so far. We will start with the seminal work by Kim. et. al. 2014 and discuss the basic idea of triggering bitflips in software. Subsequently we will discuss how to use their findings in exploits, as demonstrated by Google researchers in 2015. The results from the works of these two groups is still of vital interest for the discussion of countermeasures that now may find their way into the Linux kernel.
Another branch of attacks combine Rowhammer with other attack primitives. We will discuss attacks using deduplication (Dedup est Machina, Flip Feng Shui) and their impact. Furthermore, we will discuss the first Rowhammer attacks on cryptographic primitives that have been presented in 2016.
Finally, we will discuss countermeasures, i.e. Rowhammer detection and Rowhammer mitigation. While several countermeasures have been discussed and some have even been deployed, the problem is widely unsolved. We will shed light on the ongoing discussion amongst Linux kernel developers and point out dead ends that should be avoided in the future.
Speakers:
Dr. Clémentine Maurice and Daniel Gruss
———
👉 Subscribe to our channel:
👉 Read more about interesting IT Security topics on our blog:
✍️ Want a deeper dive?
Training courses in Single Sign-On (SAML, OAuth and OpenID Connect), Secure Web Development, TLS and Web Services are available here:
———
———
Thanks for your attention and support. Stay secure.
#cybersecurity #rowhammer #ruhrsec #cyber #talk #rowhammerbug
#conference #itsecurity #itsicherheit #JavaScriptsandbox #cryptography
🔽 More information ...
Abstract. In the past 2 years the so-called Rowhammer bug has caught the attention of many academic and non-academic researchers. The scary aspect of the Rowhammer bug is that is entirely invalidates software security assumptions. Isolation mechanisms are ineffective to a degree where an attacker can run in a website and compromise the entire host system.
In this walkthrough guide I will walk you through all Rowhammer attacks that have been presented so far. We will start with the seminal work by Kim. et. al. 2014 and discuss the basic idea of triggering bitflips in software. Subsequently we will discuss how to use their findings in exploits, as demonstrated by Google researchers in 2015. The results from the works of these two groups is still of vital interest for the discussion of countermeasures that now may find their way into the Linux kernel.
Another branch of attacks combine Rowhammer with other attack primitives. We will discuss attacks using deduplication (Dedup est Machina, Flip Feng Shui) and their impact. Furthermore, we will discuss the first Rowhammer attacks on cryptographic primitives that have been presented in 2016.
Finally, we will discuss countermeasures, i.e. Rowhammer detection and Rowhammer mitigation. While several countermeasures have been discussed and some have even been deployed, the problem is widely unsolved. We will shed light on the ongoing discussion amongst Linux kernel developers and point out dead ends that should be avoided in the future.
Speakers:
Dr. Clémentine Maurice and Daniel Gruss
———
👉 Subscribe to our channel:
👉 Read more about interesting IT Security topics on our blog:
✍️ Want a deeper dive?
Training courses in Single Sign-On (SAML, OAuth and OpenID Connect), Secure Web Development, TLS and Web Services are available here:
———
———
Thanks for your attention and support. Stay secure.
#cybersecurity #rowhammer #ruhrsec #cyber #talk #rowhammerbug
#conference #itsecurity #itsicherheit #JavaScriptsandbox #cryptography
Комментарии
 0:40:13
0:40:13
 0:18:49
0:18:49
 0:11:17
0:11:17
![[GreHack 2017] Attack](https://i.ytimg.com/vi/FiPFBWxHVmI/hqdefault.jpg) 0:26:31
0:26:31
 0:38:39
0:38:39
 0:44:45
0:44:45
 0:40:34
0:40:34
 0:10:32
0:10:32
 0:29:55
0:29:55
 0:11:04
0:11:04
 0:18:00
0:18:00
 0:33:50
0:33:50
 0:00:59
0:00:59
 0:01:34
0:01:34
 0:16:55
0:16:55
 0:20:44
0:20:44
 0:17:41
0:17:41
 0:20:08
0:20:08
![[ASPLOS19 Lightning Talk]](https://i.ytimg.com/vi/WAXiwwJMyFo/hqdefault.jpg) 0:02:27
0:02:27
 0:54:13
0:54:13
 0:08:46
0:08:46
 0:19:01
0:19:01
 0:48:20
0:48:20
 0:01:08
0:01:08