filmov
tv
Setting Up LDAP Authenticated Directory in Apache HTTPD

Показать описание
#PHP #ApacheHTTPD #ActiveDirectory #LDAP
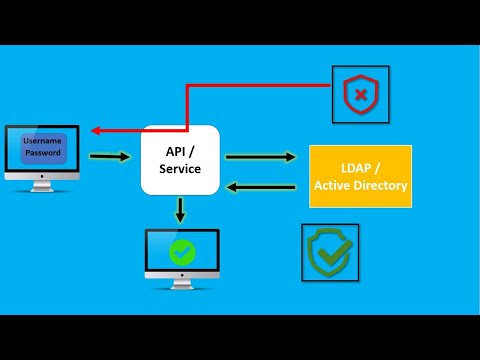
In this quick video learn how to setup LDAP/Active Directory authentication on an Apache webserver to secure web based applications.
--------------------------------------------------------------------
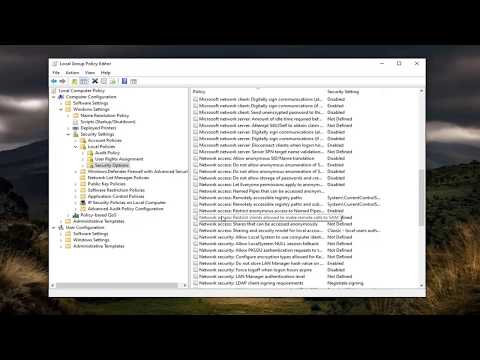
Active Directory Setup
--------------------------------------------------------------------
01. Open Active Directory Users and Computers
02. Expand the domain ≫ Users
03. Right Click Users ≫ New ≫ User
04. Create a read only account to use for LDAP binding
First Name: Read
Last Name: Only
User logon name: readonly_svc
05. Click Next
06. Set the user's password and confirm it
07. Uncheck User must change password on next logon
08. Check User cannot change password
09. Check Password never expires
10. Click Next
11. Click Finish
12. Right Click Users ≫ New ≫ Group
13. Give the group a name and click OK
14. Right Click the newly created group ≫ Properties
15. Select the Members tab ≫ Click Add...
16. Add users that will be allowed access to the web application
17. Click OK
--------------------------------------------------------------------
Configuring Apache HTTPD for LDAP
--------------------------------------------------------------------
01. Navigate to the Apache install directory/conf in Explorer
03. Find the authnz_ldap_module and make sure it is enabled by removing the # at the start of the line
04. Find the ldap_module and make sure it is enabled by removing the # at the start of the line
05. Create a Location block to enable LDAP authentication for the specified directory
≪location /ldaptest≫
# Basic authentication with LDAP against MS AD
AuthType Basic
AuthBasicProvider ldap
# AuthLDAPURL specifies the LDAP server IP, port, base DN, scope and filter
# using this format: ldap://host:port/basedn?attribute?scope?filter
# The LDAP bind username and password
AuthLDAPBindPassword "Read0nly!!"
LDAPReferrals Off
AuthUserFile /dev/null
# to authenticate a domain group, specify the full DN
AuthLDAPGroupAttributeIsDN on
require ldap-group CN=WebAuthAccess,CN=Users,DC=i12bretro,DC=local
≪/location≫
07. Restart the Apache service
08. Open a browser and navigate to the LDAP authenticated URL
09. An authentication prompt should appear, allowing only users in the AD group specified access
### Connect with me and others ###
In this quick video learn how to setup LDAP/Active Directory authentication on an Apache webserver to secure web based applications.
--------------------------------------------------------------------
Active Directory Setup
--------------------------------------------------------------------
01. Open Active Directory Users and Computers
02. Expand the domain ≫ Users
03. Right Click Users ≫ New ≫ User
04. Create a read only account to use for LDAP binding
First Name: Read
Last Name: Only
User logon name: readonly_svc
05. Click Next
06. Set the user's password and confirm it
07. Uncheck User must change password on next logon
08. Check User cannot change password
09. Check Password never expires
10. Click Next
11. Click Finish
12. Right Click Users ≫ New ≫ Group
13. Give the group a name and click OK
14. Right Click the newly created group ≫ Properties
15. Select the Members tab ≫ Click Add...
16. Add users that will be allowed access to the web application
17. Click OK
--------------------------------------------------------------------
Configuring Apache HTTPD for LDAP
--------------------------------------------------------------------
01. Navigate to the Apache install directory/conf in Explorer
03. Find the authnz_ldap_module and make sure it is enabled by removing the # at the start of the line
04. Find the ldap_module and make sure it is enabled by removing the # at the start of the line
05. Create a Location block to enable LDAP authentication for the specified directory
≪location /ldaptest≫
# Basic authentication with LDAP against MS AD
AuthType Basic
AuthBasicProvider ldap
# AuthLDAPURL specifies the LDAP server IP, port, base DN, scope and filter
# using this format: ldap://host:port/basedn?attribute?scope?filter
# The LDAP bind username and password
AuthLDAPBindPassword "Read0nly!!"
LDAPReferrals Off
AuthUserFile /dev/null
# to authenticate a domain group, specify the full DN
AuthLDAPGroupAttributeIsDN on
require ldap-group CN=WebAuthAccess,CN=Users,DC=i12bretro,DC=local
≪/location≫
07. Restart the Apache service
08. Open a browser and navigate to the LDAP authenticated URL
09. An authentication prompt should appear, allowing only users in the AD group specified access
### Connect with me and others ###
Комментарии
 0:02:53
0:02:53
 0:20:44
0:20:44
 0:14:19
0:14:19
 0:01:51
0:01:51
 0:12:49
0:12:49
 0:03:03
0:03:03
 0:06:51
0:06:51
 0:03:27
0:03:27
 0:09:27
0:09:27
 0:06:16
0:06:16
 0:02:24
0:02:24
 0:03:49
0:03:49
 0:13:59
0:13:59
 0:07:17
0:07:17
 0:26:07
0:26:07
 0:11:17
0:11:17
 0:07:25
0:07:25
 0:17:16
0:17:16
 0:06:02
0:06:02
 0:03:44
0:03:44
 0:02:13
0:02:13
 0:18:16
0:18:16
 0:26:22
0:26:22
 0:28:32
0:28:32