filmov
tv
DNS Reconnaissance and Zone Transfer: Uncovering Hidden Network Data

Показать описание
In this video, we dive into the world of DNS reconnaissance and zone transfers to uncover hidden network data. Understanding how DNS (Domain Name System) works and how attackers use it for network mapping is essential for both cybersecurity professionals and ethical hackers. By leveraging DNS enumeration techniques and performing zone transfers, you can gain valuable insights into a target's infrastructure, including subdomains, IP addresses, and other sensitive network details.
We’ll cover:
- What DNS reconnaissance is and how it helps in identifying domain-related information.
- The concept of a zone transfer and how it can expose critical data about a domain.
- Step-by-step techniques to perform DNS enumeration to gather information about domain names, subdomains, and IP ranges.
- How to detect and protect against DNS-based attacks, including unauthorized zone transfers.
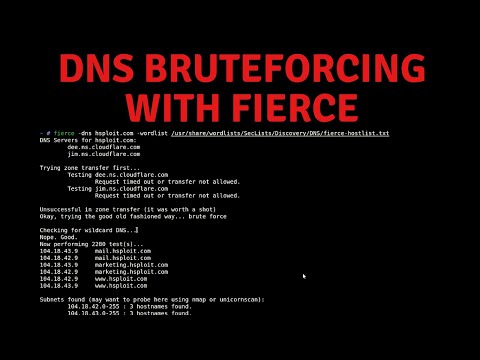
- Real-world examples and tools used for DNS reconnaissance and zone transfer (e.g., Fierce, Dig, Nslookup).
By the end of this video, you'll have a solid understanding of how DNS enumeration and zone transfers work and how you can use these techniques for network reconnaissance in penetration testing and security assessments.
🔍 What You'll Learn:
- How to perform DNS enumeration to gather domain information.
- The process of performing a zone transfer and the risks it poses to network security.
- Tools and commands for DNS reconnaissance (e.g., Dig, Nslookup, Fierce).
- Best practices for protecting your network from DNS-based vulnerabilities and attacks.
This video is ideal for those looking to expand their skills in ethical hacking, OSINT, and network security. Stay tuned for more tutorials on penetration testing, cybersecurity tools, and advanced reconnaissance techniques.
🔔 Don’t forget to like, subscribe, and hit the bell icon for more tutorials and tips on ethical hacking, network security, and cyber threat mitigation!
#DNSReconnaissance #ZoneTransfer #NetworkSecurity #EthicalHacking #PenetrationTesting #CyberSecurity #OSINT #DNSEnumeration #TechTutorial #PenTest #NetworkMapping #HackingTutorial
We’ll cover:
- What DNS reconnaissance is and how it helps in identifying domain-related information.
- The concept of a zone transfer and how it can expose critical data about a domain.
- Step-by-step techniques to perform DNS enumeration to gather information about domain names, subdomains, and IP ranges.
- How to detect and protect against DNS-based attacks, including unauthorized zone transfers.
- Real-world examples and tools used for DNS reconnaissance and zone transfer (e.g., Fierce, Dig, Nslookup).
By the end of this video, you'll have a solid understanding of how DNS enumeration and zone transfers work and how you can use these techniques for network reconnaissance in penetration testing and security assessments.
🔍 What You'll Learn:
- How to perform DNS enumeration to gather domain information.
- The process of performing a zone transfer and the risks it poses to network security.
- Tools and commands for DNS reconnaissance (e.g., Dig, Nslookup, Fierce).
- Best practices for protecting your network from DNS-based vulnerabilities and attacks.
This video is ideal for those looking to expand their skills in ethical hacking, OSINT, and network security. Stay tuned for more tutorials on penetration testing, cybersecurity tools, and advanced reconnaissance techniques.
🔔 Don’t forget to like, subscribe, and hit the bell icon for more tutorials and tips on ethical hacking, network security, and cyber threat mitigation!
#DNSReconnaissance #ZoneTransfer #NetworkSecurity #EthicalHacking #PenetrationTesting #CyberSecurity #OSINT #DNSEnumeration #TechTutorial #PenTest #NetworkMapping #HackingTutorial
Комментарии
 0:13:55
0:13:55
 0:07:28
0:07:28
 0:11:33
0:11:33
 0:20:52
0:20:52
 0:23:12
0:23:12
 0:02:17
0:02:17
 0:05:36
0:05:36
 0:03:16
0:03:16
 0:07:09
0:07:09
 0:07:24
0:07:24
 0:10:41
0:10:41
 0:09:24
0:09:24
 0:19:23
0:19:23
 0:05:38
0:05:38
 0:02:52
0:02:52
 0:04:48
0:04:48
 0:10:51
0:10:51
 0:11:06
0:11:06
 0:58:15
0:58:15
 0:26:25
0:26:25
 0:03:46
0:03:46
 0:06:13
0:06:13
 0:07:28
0:07:28
 0:07:09
0:07:09