filmov
tv
is this exploit over hyped? (9.8 CVSS btw)

Показать описание
Go show Simone some love. Also, disable cupsd.
is this exploit over hyped? (9.8 CVSS btw)
Sheet mask HACK for a perfect fit. You NEED to try this! | Dr Adel #shorts
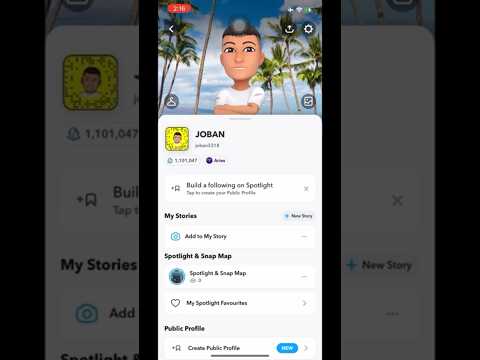
1.1 Million score in 15 seconds | Snapchat score hack | Free | IOS & Android
Mrunal Panchal CAUGHT LYING & EXPLOITING her Customers| Over-Priced & Over-Hyped?
trying the viral tattoo hack
Can A Flipper Zero Hack A PHONE? #Shorts
My BIGGEST Dairy Queen ice cream hack
Viral Eyelash Hack 🤞
Throne and Liberty - CASTLE SIEGE HYPE | Universal Basic Income Alliance | Xeroth Server
Quick HACK for a perfect SKIN texture! #drawing #oppenheimer
I HIRED A Da Hood Egirl & Trolled Her WITH EXPLOITS! *She Cried*
HACK To WIN at a Rigged Claw Machine #shorts
Foot Peel Mask || TIKTOK HACK || #shorts
Best mom and dad hack! How to prevent baby poop blowouts! #mom #momhack #lifehack #hack
trying the CRAZY pineapple HACK!!
Nintendo Switch secrets 🤫. Free games hack!
Hyperrealistic Cake Hack!
Try this Hair Hack Tomorrow ✨🫶🏼✨ #hair #hairstyle #shorts #longhair #haircare
Viral Eyelash Hack #makeup #makeuphacks #viralvideo #eyelashhack #eyelash #liner #shorts
✨EASY HACK✨ to crop your tank tops WITHOUT cutting it! 🙅🏼♀️👀 #shorts
Useful styling hack #stylehacks #stylinghacks #styling #jeans
Have you ever tried this?? Nutella Food Hack
This Eyeliner Hack is a GAME CHANGER! Perfect for Mature Eyes!
Lipstick on Pigmented Lips!? Try this HACK ✨ #shorts #makeup #makeuphacks
Комментарии
 0:13:50
0:13:50
 0:00:23
0:00:23
 0:00:16
0:00:16
 0:04:02
0:04:02
 0:00:15
0:00:15
 0:00:44
0:00:44
 0:00:20
0:00:20
 0:00:08
0:00:08
 0:02:33
0:02:33
 0:00:35
0:00:35
 0:09:06
0:09:06
 0:00:30
0:00:30
 0:00:33
0:00:33
 0:00:09
0:00:09
 0:00:55
0:00:55
 0:00:36
0:00:36
 0:00:25
0:00:25
 0:00:24
0:00:24
 0:00:16
0:00:16
 0:00:16
0:00:16
 0:00:35
0:00:35
 0:00:16
0:00:16
 0:00:59
0:00:59
 0:00:14
0:00:14