filmov
tv
what is jwt token authentication | attacking jwt for beginners

Показать описание
what is #jwt - JSON Web Token. JSON Web Token (JWT) is a compact URL-safe means of representing claims to be transferred between two parties.
How is JWT token generated?
How is a JWT token generated? We set the signing algorithm to be HMAC SHA256 (JWT supports multiple algorithms), then we create a buffer from this JSON-encoded object, and we encode it using base64.
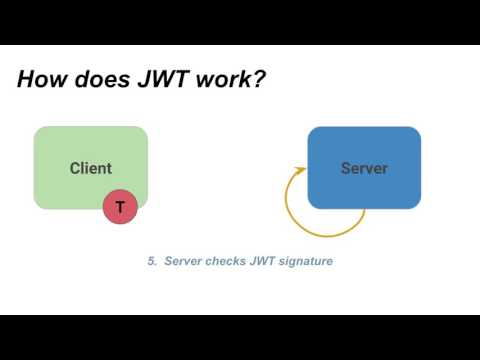
working of jwt.
the server generates a token that certifies the user identity, and sends it to the client.
Vulnmachines - Place for Pentesters
Vulnmachines is online cyber security training platform with a massive number of labs, allowing individuals, students, cyber professionals, companies, universities and all kinds of organizations around the world to enhance their practical skills with Real-world enterprise scenarios.
TheSecOps Group : The SecOps Group is founded by industry veterans. We have over 15 years of experience in providing cyber security consultancy and have worked with some of the largest blue chip companies. Being an independent boutique company, we enable our customers to continuously identify and assess their security postures and provide advice in securing against the adversaries.
Our team regularly speaks at international conferences (including Black Hat, Defcon, HITB, and OWASP Appsec). We pride ourselves in hiring the best talent and our passion is to stay up-to-date with the latest in the world of ethical hacking.
Follow us
#infosec #cybersecurity #cyber #pentesting #cve #exploit #django #pentest #bugbounty #bugbountytips #vulnerability #information #owasptop10
json web token with practical
jwt with practical
jwt attack
jwt vulnerability
jwt exploit
how to use jwt cracker
#jwt #beginnersjwt #attackonjwt #infosec #cybersecurity #owasptop10
How is JWT token generated?
How is a JWT token generated? We set the signing algorithm to be HMAC SHA256 (JWT supports multiple algorithms), then we create a buffer from this JSON-encoded object, and we encode it using base64.
working of jwt.
the server generates a token that certifies the user identity, and sends it to the client.
Vulnmachines - Place for Pentesters
Vulnmachines is online cyber security training platform with a massive number of labs, allowing individuals, students, cyber professionals, companies, universities and all kinds of organizations around the world to enhance their practical skills with Real-world enterprise scenarios.
TheSecOps Group : The SecOps Group is founded by industry veterans. We have over 15 years of experience in providing cyber security consultancy and have worked with some of the largest blue chip companies. Being an independent boutique company, we enable our customers to continuously identify and assess their security postures and provide advice in securing against the adversaries.
Our team regularly speaks at international conferences (including Black Hat, Defcon, HITB, and OWASP Appsec). We pride ourselves in hiring the best talent and our passion is to stay up-to-date with the latest in the world of ethical hacking.
Follow us
#infosec #cybersecurity #cyber #pentesting #cve #exploit #django #pentest #bugbounty #bugbountytips #vulnerability #information #owasptop10
json web token with practical
jwt with practical
jwt attack
jwt vulnerability
jwt exploit
how to use jwt cracker
#jwt #beginnersjwt #attackonjwt #infosec #cybersecurity #owasptop10
Комментарии
 0:14:53
0:14:53
 0:05:13
0:05:13
 0:01:07
0:01:07
 0:05:14
0:05:14
 0:07:52
0:07:52
 0:02:18
0:02:18
 0:07:00
0:07:00
 0:04:30
0:04:30
 0:29:51
0:29:51
 0:11:24
0:11:24
 0:14:53
0:14:53
 0:11:27
0:11:27
 0:26:12
0:26:12
 0:14:47
0:14:47
 0:27:36
0:27:36
 0:10:25
0:10:25
 0:11:53
0:11:53
 0:10:20
0:10:20
 1:41:00
1:41:00
![[HINDI] Introduction to](https://i.ytimg.com/vi/5mUDRQfwXuE/hqdefault.jpg) 0:19:13
0:19:13
 0:18:28
0:18:28
 0:14:30
0:14:30
 0:23:45
0:23:45
 0:05:59
0:05:59