filmov
tv
your software is too fuzzy

Показать описание
Did you know you can just SCREAM at your code to find bugs? Yeah seriously it's that easy. In this video we'll talk about libfuzzer, which is a simple to use tool to write code that finds bugs in your code. In this video we write some code, find a bug, and patch it.
🔥🔥🔥 SOCIALS 🔥🔥🔥
🔥🔥🔥 SOCIALS 🔥🔥🔥
your software is too fuzzy
How to Make Your Android Phone Look Like an iPhone #Shorts
Fuzzy Keymixing 101 #Short
BLURRY PHOTOS? 😰 Here's how to fix it!
How to get rid of brain fog, every single day (Part 1)
Does FPS drop in your AMD graphics card? Try this setting
Fix for fuzzy text with MacOS UI scaling on external displays
Avoid Ruining Your Video Quality: CapCut Export Tips and Tricks
NODES 2024 Best Of: GenAI
Here’s why your artwork is pixelated / Procreate tips and tricks
GitHub Protip: fuzzy file search
mic monitoring explained
Fuzzy file finder allows you to search repos super fast! Did you know about it? 🔎
Top 4 Fuzzy CLIs
Fuzzy Dice In Blender!!!
I'm sorry, little ones 😔 #tofucute #plushies #plush #kawaii #kawaiiplush #plushtoys #kawaiishop...
TURN OFF HDR ON YOUR IPHONE FOR BETTER UPLOAD QUALITY 👀
Fuzzy Search v2 - Even MORE Fuzzy Search features now available!
Fzf: Can Do Far More Than Just Fuzzy Find Your Files
Mythic + Gifted Auto Jelly... #shorts
Is your image blurry? 😓
This is decent vim fuzzy search plugin
Code editor hacks every developer wishes they knew sooner! #programming #vscode #webdevelopment
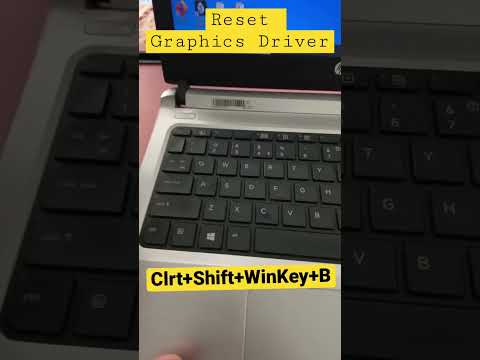
Screen Freeze | Laptop Screen Freeze or Stuck | Reset Graphics Driver
Комментарии
 0:08:34
0:08:34
 0:00:20
0:00:20
 0:00:30
0:00:30
 0:00:26
0:00:26
 0:00:58
0:00:58
 0:00:27
0:00:27
 0:03:57
0:03:57
 0:00:39
0:00:39
 0:42:27
0:42:27
 0:00:31
0:00:31
 0:00:31
0:00:31
 0:00:18
0:00:18
 0:00:22
0:00:22
 0:04:31
0:04:31
 0:00:12
0:00:12
 0:00:22
0:00:22
 0:00:30
0:00:30
 0:05:55
0:05:55
 0:19:36
0:19:36
 0:00:17
0:00:17
 0:00:15
0:00:15
 0:08:57
0:08:57
 0:00:48
0:00:48
 0:00:33
0:00:33