filmov
tv
Authentication and Authorization in a Microservice Architecture | OAuth 2.0 | JWT

Показать описание
In this video tutorial, we will be looking into:
1) How Authentication and Authorization work in a Microservice Architecture?
2) What problems do we face when performing Authentication in Microservices?
3) What could be the best possible solution to Authentication and Authorization in Microservices?
Connect with me here:
Chapters:
00:00 - Introduction
00:41 - What do we mean by Authentication and Authorization?
01:11 - Authentication and Authorization in a Monolithic Architecture
02:45 - Problems we face in Microservices Authentication & Authorization
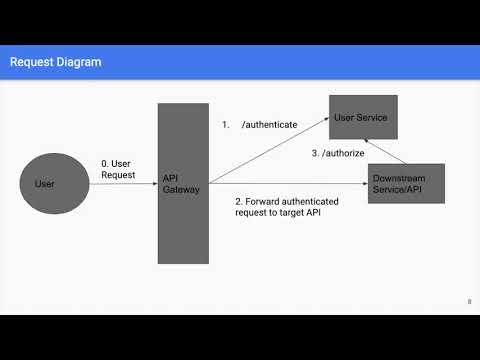
05:08 - Recommended solution to Authentication & Authorization in Microservices
06:11 - Solution - Step (1) - Authenticate with an API using a client_id and a client_secret
07:00 - Solution - Step (2) - Create an access token and return the token to the client application
07:44 - Solution - Step (3) - Verify the access token
#Microservices #MicroserviceArchitecture #SystemDesign
1) How Authentication and Authorization work in a Microservice Architecture?
2) What problems do we face when performing Authentication in Microservices?
3) What could be the best possible solution to Authentication and Authorization in Microservices?
Connect with me here:
Chapters:
00:00 - Introduction
00:41 - What do we mean by Authentication and Authorization?
01:11 - Authentication and Authorization in a Monolithic Architecture
02:45 - Problems we face in Microservices Authentication & Authorization
05:08 - Recommended solution to Authentication & Authorization in Microservices
06:11 - Solution - Step (1) - Authenticate with an API using a client_id and a client_secret
07:00 - Solution - Step (2) - Create an access token and return the token to the client application
07:44 - Solution - Step (3) - Verify the access token
#Microservices #MicroserviceArchitecture #SystemDesign
Authentication vs Authorization Explained
Session vs Token Authentication in 100 Seconds
Authentication, Authorization, and Accounting - CompTIA Security+ SY0-701 - 1.2
'Basic Authentication' in Five Minutes
Authentication Vs Authorization in plain English - Security - Session 1
Five Spring Security Concepts - Authentication vs authorization - Java Brains Brain Bytes
Microservices Authentication/Authorization architectural pattern
Authentication vs Authorization
You Won't Believe the POWER of User Authentication
ASP.NET Authentication using Identity in 10 Minutes - Authentication and Authorization in .NET8
What's the difference between Authentication vs Authorization?
The A to Z of API AuthoriZation
Part 14: Authorization and Authentication in APIs | Postman Authorization and Authentication
Why do we have Authorization and NOT Authentication in API Requests
Authentication & Authorization in Microservice Architectures
ASP.NET Core Authentication and Authorization - the Key Concepts - Anders Abel - NDC Oslo 2024
Explain Authentication and Authorization - AZ-900 Certification Course
Authentication vs Authorization in Telugu | Hemendra | CodeZon
Authentication & Authorization | Bcrypt | JWT | Part 14 - Backend Development
Difference between Authentication and Authorization in Hindi
#156 How Authentication Works | Angular Authentication & Authorization | A Complete Angular Cour...
How to Authorize User Roles and Permissions | Node.js & Express Authorization Tutorial
Difference between Authentication and Authorization? (Software Testing Interview Question #150)
What is Identification, Authentication, Authorization, Auditing, Accountability| IAAA| Cybersecurity
Комментарии
 0:03:41
0:03:41
 0:02:18
0:02:18
 0:09:04
0:09:04
 0:05:07
0:05:07
 0:02:20
0:02:20
 0:11:37
0:11:37
 0:10:03
0:10:03
 0:01:00
0:01:00
 0:01:23
0:01:23
 0:12:22
0:12:22
 0:04:12
0:04:12
 0:17:23
0:17:23
 0:18:39
0:18:39
 0:04:28
0:04:28
 0:05:01
0:05:01
 0:59:09
0:59:09
 0:03:52
0:03:52
 0:04:16
0:04:16
 0:40:50
0:40:50
 0:02:03
0:02:03
 0:09:27
0:09:27
 0:29:05
0:29:05
 0:03:10
0:03:10
 0:09:56
0:09:56