filmov
tv
Calling Conventions For Reverse Engineering GODS

Показать описание
🔥 Learn How Calling Conventions Work For Reverse Engineering & Game Hacking
📜 Video Description:
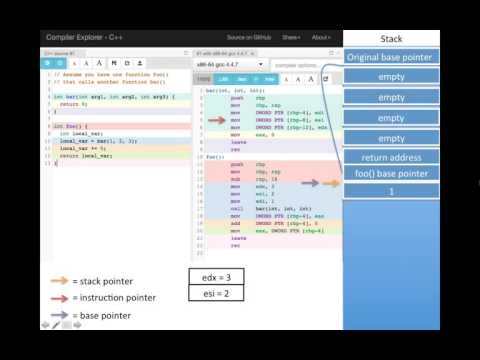
Today we're going to explore the low level world of calling conventions, which are essentially the guidelines that dictate how function arguments are passed. Understanding calling conventions is key to comprehending assembly code, especially when you're involved in reverse engineering tasks. It's important to recognize how the stack operates, growing and shrinking through various push and pop instructions. Remember, the stack is just one segment within a process's memory, with others like the heap, code, and data sections playing their pivotal roles.
📝 Timestamps:
00:00 Intro to Calling Conventions
00:16 Stack Mechanics
01:16 Malcore Is Dank
02:17 Function Prologue
03:00 cdecl calling convention
04:01 AddNum Example
05:00 cdecl Cleanup
05:30 stdcall
06:01 FastCall Variants
07:28 Microsoft FastCall
07:47 thiscall Convention
✏️ Tags:
#reverseengineering #gamehacking #malwareanalysis
thiscall calling convention
cdecl calling convention
calling convention x64
reverse engineering
x64 calling convention
x86 calling convention
calling convention
x86 calling conventions
calling convention x86
reverse engineering
x86-64 calling convention
c++ calling conventions
c++ calling convention
fastcall calling convention
stdcall calling convention
reverse engineering
windows calling convention
calling conventions
function calling convention
calling conventions c++
📜 Video Description:
Today we're going to explore the low level world of calling conventions, which are essentially the guidelines that dictate how function arguments are passed. Understanding calling conventions is key to comprehending assembly code, especially when you're involved in reverse engineering tasks. It's important to recognize how the stack operates, growing and shrinking through various push and pop instructions. Remember, the stack is just one segment within a process's memory, with others like the heap, code, and data sections playing their pivotal roles.
📝 Timestamps:
00:00 Intro to Calling Conventions
00:16 Stack Mechanics
01:16 Malcore Is Dank
02:17 Function Prologue
03:00 cdecl calling convention
04:01 AddNum Example
05:00 cdecl Cleanup
05:30 stdcall
06:01 FastCall Variants
07:28 Microsoft FastCall
07:47 thiscall Convention
✏️ Tags:
#reverseengineering #gamehacking #malwareanalysis
thiscall calling convention
cdecl calling convention
calling convention x64
reverse engineering
x64 calling convention
x86 calling convention
calling convention
x86 calling conventions
calling convention x86
reverse engineering
x86-64 calling convention
c++ calling conventions
c++ calling convention
fastcall calling convention
stdcall calling convention
reverse engineering
windows calling convention
calling conventions
function calling convention
calling conventions c++
 0:09:26
0:09:26
 0:21:37
0:21:37
 0:20:17
0:20:17
 0:18:13
0:18:13
 0:15:40
0:15:40
 0:20:45
0:20:45
 0:11:04
0:11:04
 0:07:45
0:07:45
 0:03:16
0:03:16
 0:00:56
0:00:56
 0:17:30
0:17:30
 0:25:26
0:25:26
 1:36:10
1:36:10
 0:02:59
0:02:59
 0:14:05
0:14:05
 0:17:45
0:17:45
 0:20:20
0:20:20
 0:01:00
0:01:00
 0:29:49
0:29:49
 0:01:00
0:01:00
 0:14:58
0:14:58
 0:09:48
0:09:48
 0:26:54
0:26:54
 0:01:28
0:01:28