filmov
tv
how hackers bypass file upload restrictions!

Показать описание
// Membership //
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
how hackers bypass file upload restrictions!
File Upload Vulnerabilities & Filter Bypass
How To Bypass Website File Upload Restrictions
Bypass File Upload Restrictions using Magic Bytes
Filters Bypass Web App directory/file | Bug Bounty | Ethical Hacking
Unrestricted File Upload | bypass upload restriction | Hackerone
Bug Bounty PoC: FIle Upload Restriction Bypass
Bypass Server Upload Restrictions & Create a Reverse Shell [Tutorial]
Ob45 Magic Bullet + Hologram | Free Fire Anti Blacklist Cs Rank Working Data Config File
Bypass File Upload Restriction
Bypass File Upload - Burpsuite
How Hackers Bypass Kernel Anti Cheat
Basic File Upload Bypass Techniques
Web Shell Upload via Content-Type Restriction Bypass
Bypass Shell Upload via .htaccess
how to bypass high level security & exploiting file upload vulnerability to hack target web ser...
how hackers bypass login pages!
3 Easy Tricks to Bypass Cloudflare WAF For File Upload || Bug Bounty || 403 Bypass || WAF Bypass ||#
pro hacker teaches you how to bypass this!
Authenticated/Unauthenticated File upload bypass (Shell Upload Vulnerability)
how hackers bypass windows login screen!
File Upload 🧐🧐 Vulnerability Bypass ! Bug bounty #cybersecurity |
IMG FILE UPLOAD BYPASS - BURP SUİTE
File upload Vulnerabilities (Bypass Content type restriction)
Комментарии
 0:05:39
0:05:39
 0:20:10
0:20:10
 0:20:18
0:20:18
 0:07:20
0:07:20
 0:07:01
0:07:01
 0:00:46
0:00:46
 0:00:41
0:00:41
 0:12:51
0:12:51
 0:02:07
0:02:07
 0:05:57
0:05:57
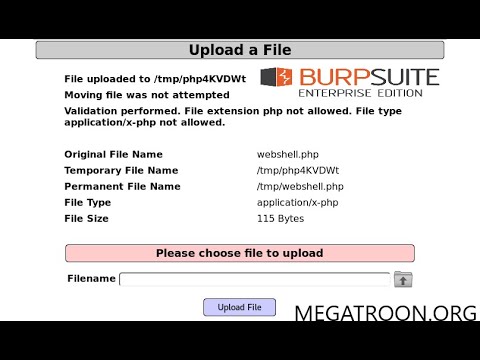 0:05:07
0:05:07
 0:19:38
0:19:38
 0:22:25
0:22:25
 0:11:30
0:11:30
 0:05:22
0:05:22
 0:16:03
0:16:03
 0:08:04
0:08:04
 0:03:17
0:03:17
 0:08:12
0:08:12
 0:12:35
0:12:35
 0:07:36
0:07:36
 0:05:16
0:05:16
 0:02:19
0:02:19
 0:04:46
0:04:46