filmov
tv
Understanding the PE+ File Format - Part 4: Entry Points and TLS Callbacks

Показать описание
In Part 4, we focus on the PE+ file format's entry points, specifically the AddressOfEntryPoint and TLS callbacks. The video covers how to find the AddressOfEntryPoint, its role, and entry points' precedence. It also explains locating the IMAGE_TLS_DIRECTORY, enumerating TLS callbacks, and the tools used, including Hiew and an IDAPython script, due to IDA's limitations in viewing these details directly. The session wraps up with a demonstration on dumping TLS entry points for all loaded modules, providing insights into analyzing these crucial elements without unnecessary complexity.
Table of Contents:
00:04 - Introduction
00:24 - PE entrypoints are detected by IDA but only for the input file
01:15 - Inspecting entry points of running processes
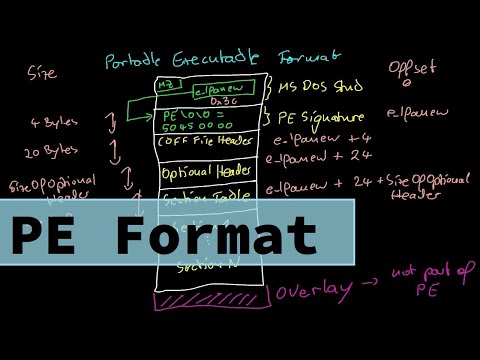
01:44 - Starting from the image base / IMAGE_DOS_HEADER
02:16 - Importing the needed standard types (from the Windows SDK headers / TIL)
02:51 - Applying the needed structures
03:11 - Locating the "AddressOfEntryPoint"
03:42 - Understanding entry points precedence
04:36 - Locating the TLS data directory
06:49 - Interpreting the IMAGE_TLS_DIRECTORY
07:56 - IMAGE_TLS_DIRECTORY.AddressOfCallbacks are already relocated
08:33 - Enumerating the TLS callbacks entry points
09:16 - TLS callback prototype is the same as DllMain prototype
09:43 - No built-in in way in IDA to see entry points and TLS callbacks
10:06 - Using Hiew to inspect the TLS callbacks
10:55 - IDAPython script to discover entry points
14:02 - Dumping all TLS entry points for all loaded modules
14:22 - Testing the script
15:11 - NTDLL has no entry point
16:07 - Recap
Resources:
Table of Contents:
00:04 - Introduction
00:24 - PE entrypoints are detected by IDA but only for the input file
01:15 - Inspecting entry points of running processes
01:44 - Starting from the image base / IMAGE_DOS_HEADER
02:16 - Importing the needed standard types (from the Windows SDK headers / TIL)
02:51 - Applying the needed structures
03:11 - Locating the "AddressOfEntryPoint"
03:42 - Understanding entry points precedence
04:36 - Locating the TLS data directory
06:49 - Interpreting the IMAGE_TLS_DIRECTORY
07:56 - IMAGE_TLS_DIRECTORY.AddressOfCallbacks are already relocated
08:33 - Enumerating the TLS callbacks entry points
09:16 - TLS callback prototype is the same as DllMain prototype
09:43 - No built-in in way in IDA to see entry points and TLS callbacks
10:06 - Using Hiew to inspect the TLS callbacks
10:55 - IDAPython script to discover entry points
14:02 - Dumping all TLS entry points for all loaded modules
14:22 - Testing the script
15:11 - NTDLL has no entry point
16:07 - Recap
Resources:
Комментарии
 0:11:28
0:11:28
 0:04:20
0:04:20
 0:06:29
0:06:29
 0:03:14
0:03:14
 0:22:30
0:22:30
 0:07:33
0:07:33
 0:10:03
0:10:03
 0:40:45
0:40:45
 0:23:48
0:23:48
 0:08:50
0:08:50
 1:03:04
1:03:04
 0:10:52
0:10:52
 0:12:30
0:12:30
 0:25:02
0:25:02
 0:35:02
0:35:02
 0:10:03
0:10:03
 0:12:19
0:12:19
 0:19:02
0:19:02
 0:06:39
0:06:39
 0:18:58
0:18:58
 0:01:10
0:01:10
 0:10:23
0:10:23
 0:02:13
0:02:13
 0:32:21
0:32:21