filmov
tv
How to Use AWS Secrets Manager with SecretProviderClass in Kubernetes

Показать описание
Learn how to correctly configure environment variables from AWS Secrets Manager in Kubernetes using SecretProviderClass. Ensure your secrets are accessible in your pods!
---
Visit these links for original content and any more details, such as alternate solutions, latest updates/developments on topic, comments, revision history etc. For example, the original title of the Question was: Env variable from AWS Secrets Manager in Kubernetes
If anything seems off to you, please feel free to write me at vlogize [AT] gmail [DOT] com.
---
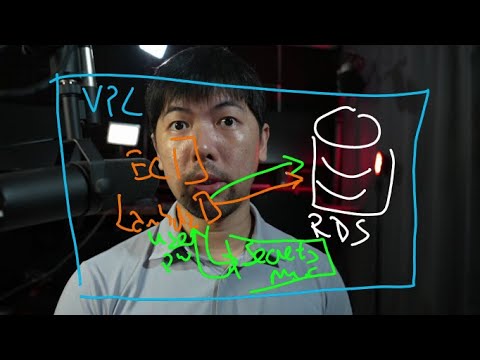
Using AWS Secrets Manager with SecretProviderClass in Kubernetes
Managing secrets efficiently is crucial for the security of any application. If you're using Amazon EKS (Elastic Kubernetes Service) and aiming to access secrets stored in AWS Secrets Manager through Kubernetes, you might run into some challenges. One common issue is getting those secrets to show up correctly as environment variables in your containerized applications. In this guide, we'll walk through a solution to this problem and ensure you can leverage AWS Secrets Manager without a hitch.
The Problem
In a recent inquiry, a user reported difficulties in accessing AWS Secret Manager secrets as environment variables within a Kubernetes pod. While secrets were being successfully mounted inside the container, attempts to set them as environment variables led to an error stating that the secret was not found. Specifically, the user was seeing the output of the secret stored in the mounted volume but running into challenges when trying to reference it via SecretKeyRef in the deployment configuration.
This can be frustrating, especially if you’ve set up your configurations but fail to see the expected outcomes.
Understanding the Configuration
Let's break down the configuration to understand where the misalignment may have occurred.
SecretProviderClass
The configuration for SecretProviderClass defines how secrets are fetched from AWS Secrets Manager. Here’s a brief look at a correct setup:
[[See Video to Reveal this Text or Code Snippet]]
In this configuration, it’s essential that the secretName in secretObjects corresponds accurately to the name referenced elsewhere in your application.
Deployment Configuration
Here's how the deployment looks where the error was occurring:
[[See Video to Reveal this Text or Code Snippet]]
This configuration is mostly correct; however, if the associated secret is not created in Kubernetes, the application fails to run.
The Solution
After a careful review of the setup and some troubleshooting, the solution came down to a specific installation setting when deploying the secrets-store-csi-driver. The user found that they did not enable a crucial helm value that allows Kubernetes to synchronize secrets.
Key Steps to Resolve the Issue
Uninstall the Existing Driver: If you had previously installed the secrets-store-csi-driver, you need to remove it first.
[[See Video to Reveal this Text or Code Snippet]]
[[See Video to Reveal this Text or Code Snippet]]
Verify Secret Availability: Once reinstalled, you can check if the secret is available:
[[See Video to Reveal this Text or Code Snippet]]
You should now see the awscredentials available in the Kubernetes namespace.
Conclusion
Now, you can deploy your services confidently, knowing your secrets are well-managed and accessible!
---
Visit these links for original content and any more details, such as alternate solutions, latest updates/developments on topic, comments, revision history etc. For example, the original title of the Question was: Env variable from AWS Secrets Manager in Kubernetes
If anything seems off to you, please feel free to write me at vlogize [AT] gmail [DOT] com.
---
Using AWS Secrets Manager with SecretProviderClass in Kubernetes
Managing secrets efficiently is crucial for the security of any application. If you're using Amazon EKS (Elastic Kubernetes Service) and aiming to access secrets stored in AWS Secrets Manager through Kubernetes, you might run into some challenges. One common issue is getting those secrets to show up correctly as environment variables in your containerized applications. In this guide, we'll walk through a solution to this problem and ensure you can leverage AWS Secrets Manager without a hitch.
The Problem
In a recent inquiry, a user reported difficulties in accessing AWS Secret Manager secrets as environment variables within a Kubernetes pod. While secrets were being successfully mounted inside the container, attempts to set them as environment variables led to an error stating that the secret was not found. Specifically, the user was seeing the output of the secret stored in the mounted volume but running into challenges when trying to reference it via SecretKeyRef in the deployment configuration.
This can be frustrating, especially if you’ve set up your configurations but fail to see the expected outcomes.
Understanding the Configuration
Let's break down the configuration to understand where the misalignment may have occurred.
SecretProviderClass
The configuration for SecretProviderClass defines how secrets are fetched from AWS Secrets Manager. Here’s a brief look at a correct setup:
[[See Video to Reveal this Text or Code Snippet]]
In this configuration, it’s essential that the secretName in secretObjects corresponds accurately to the name referenced elsewhere in your application.
Deployment Configuration
Here's how the deployment looks where the error was occurring:
[[See Video to Reveal this Text or Code Snippet]]
This configuration is mostly correct; however, if the associated secret is not created in Kubernetes, the application fails to run.
The Solution
After a careful review of the setup and some troubleshooting, the solution came down to a specific installation setting when deploying the secrets-store-csi-driver. The user found that they did not enable a crucial helm value that allows Kubernetes to synchronize secrets.
Key Steps to Resolve the Issue
Uninstall the Existing Driver: If you had previously installed the secrets-store-csi-driver, you need to remove it first.
[[See Video to Reveal this Text or Code Snippet]]
[[See Video to Reveal this Text or Code Snippet]]
Verify Secret Availability: Once reinstalled, you can check if the secret is available:
[[See Video to Reveal this Text or Code Snippet]]
You should now see the awscredentials available in the Kubernetes namespace.
Conclusion
Now, you can deploy your services confidently, knowing your secrets are well-managed and accessible!
 0:06:16
0:06:16
 0:24:12
0:24:12
 0:33:50
0:33:50
 0:04:36
0:04:36
 0:01:26
0:01:26
 0:04:43
0:04:43
 0:12:45
0:12:45
 0:05:31
0:05:31
 0:16:42
0:16:42
 0:05:27
0:05:27
 0:08:04
0:08:04
 0:09:35
0:09:35
 0:03:37
0:03:37
 0:02:57
0:02:57
 0:06:22
0:06:22
 0:14:32
0:14:32
 0:23:29
0:23:29
 0:11:01
0:11:01
 0:31:01
0:31:01
 0:18:09
0:18:09
 0:07:55
0:07:55
 0:05:57
0:05:57
 0:42:06
0:42:06
 0:02:22
0:02:22