filmov
tv
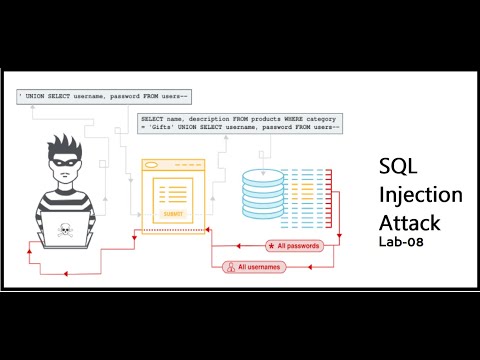
SQL injection attack, querying the database type and version on Oracle - Lab#06

Показать описание
In this walkthrough, we exploit a SQL injection vulnerability in the product category filter to determine the database type and version, specifically for Oracle databases.
🎯 Lab Objective:
Use a UNION-based SQL injection to retrieve and display the Oracle database version string in the application's response.
🔍 Oracle-Specific Insight:
Unlike other databases, Oracle requires a FROM DUAL clause when selecting constants or system functions. To get the version, you can use:
UNION SELECT banner FROM v$version
UNION SELECT version FROM v$instance
💡 Steps Covered:
Identify the number of columns and string-compatible columns (from earlier labs)
Craft an Oracle-compatible UNION SELECT payload
Inject the payload to retrieve and display the version string in the UI
Submit the lab when the version string appears on the page
📘 Why This Matters:
Fingerprinting the database is a critical step in building more advanced SQL injection payloads, especially for DB-specific exploits or bypasses.
#Oracle #SQLInjection #DatabaseFingerprinting #WebSecurityAcademy #PortSwigger #OWASP #InfoSec #PenTesting #CyberSecurity #UNIONAttack #EthicalHacking #SQLiExploit
🎯 Lab Objective:
Use a UNION-based SQL injection to retrieve and display the Oracle database version string in the application's response.
🔍 Oracle-Specific Insight:
Unlike other databases, Oracle requires a FROM DUAL clause when selecting constants or system functions. To get the version, you can use:
UNION SELECT banner FROM v$version
UNION SELECT version FROM v$instance
💡 Steps Covered:
Identify the number of columns and string-compatible columns (from earlier labs)
Craft an Oracle-compatible UNION SELECT payload
Inject the payload to retrieve and display the version string in the UI
Submit the lab when the version string appears on the page
📘 Why This Matters:
Fingerprinting the database is a critical step in building more advanced SQL injection payloads, especially for DB-specific exploits or bypasses.
#Oracle #SQLInjection #DatabaseFingerprinting #WebSecurityAcademy #PortSwigger #OWASP #InfoSec #PenTesting #CyberSecurity #UNIONAttack #EthicalHacking #SQLiExploit
 0:12:35
0:12:35
 0:06:20
0:06:20
 0:02:46
0:02:46
 0:03:30
0:03:30
 0:04:40
0:04:40
 0:00:33
0:00:33
 0:09:08
0:09:08
 0:27:04
0:27:04
 0:02:11
0:02:11
 0:05:25
0:05:25
 0:17:11
0:17:11
 0:06:15
0:06:15
 0:04:25
0:04:25
 0:04:43
0:04:43
 0:02:06
0:02:06
 0:06:42
0:06:42
 0:00:36
0:00:36
 0:01:19
0:01:19
 0:05:21
0:05:21
 0:09:44
0:09:44
 0:01:16
0:01:16
 0:06:20
0:06:20
 0:04:14
0:04:14
 0:06:36
0:06:36